Ultimate Combo: Cloud Attack Emulation meets Microsoft Sentinel


Organizations leveraging modern architectures continuously grapple with sophisticated attacks that often bypass preventive controls. Consequently, the need for effective detection and response capabilities has never been more critical. This article delves into the powerful synergy between Microsoft Azure Sentinel, a leading cloud-native SIEM, and Mitigant Cloud Attack Emulation (CAE), an advanced adversary emulation platform for cloud-native infrastructures. Together, these cloud-native security products form an ultimate combo, empowering security teams to mature their detection engineering efforts, reduce alert fatigue, and bolster their overall cloud security posture. More importantly, this synergy allows teams to be proactive, enabling them to stay ahead of potential threats.
Microsoft Sentinel Overview
Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) that provides a platform for cyberthreat detection, investigation, response, and proactive hunting. It affords a bird's-eye view across the entire enterprise infrastructure, including multi-cloud and hybrid environments. Sentinel allows security teams to ingest data from various sources, analyze it for suspicious activities, and automate responses to emerging threats. Its ability to leverage the power of the cloud offers unparalleled scalability and flexibility, adapting to the ever-growing volume of security data.
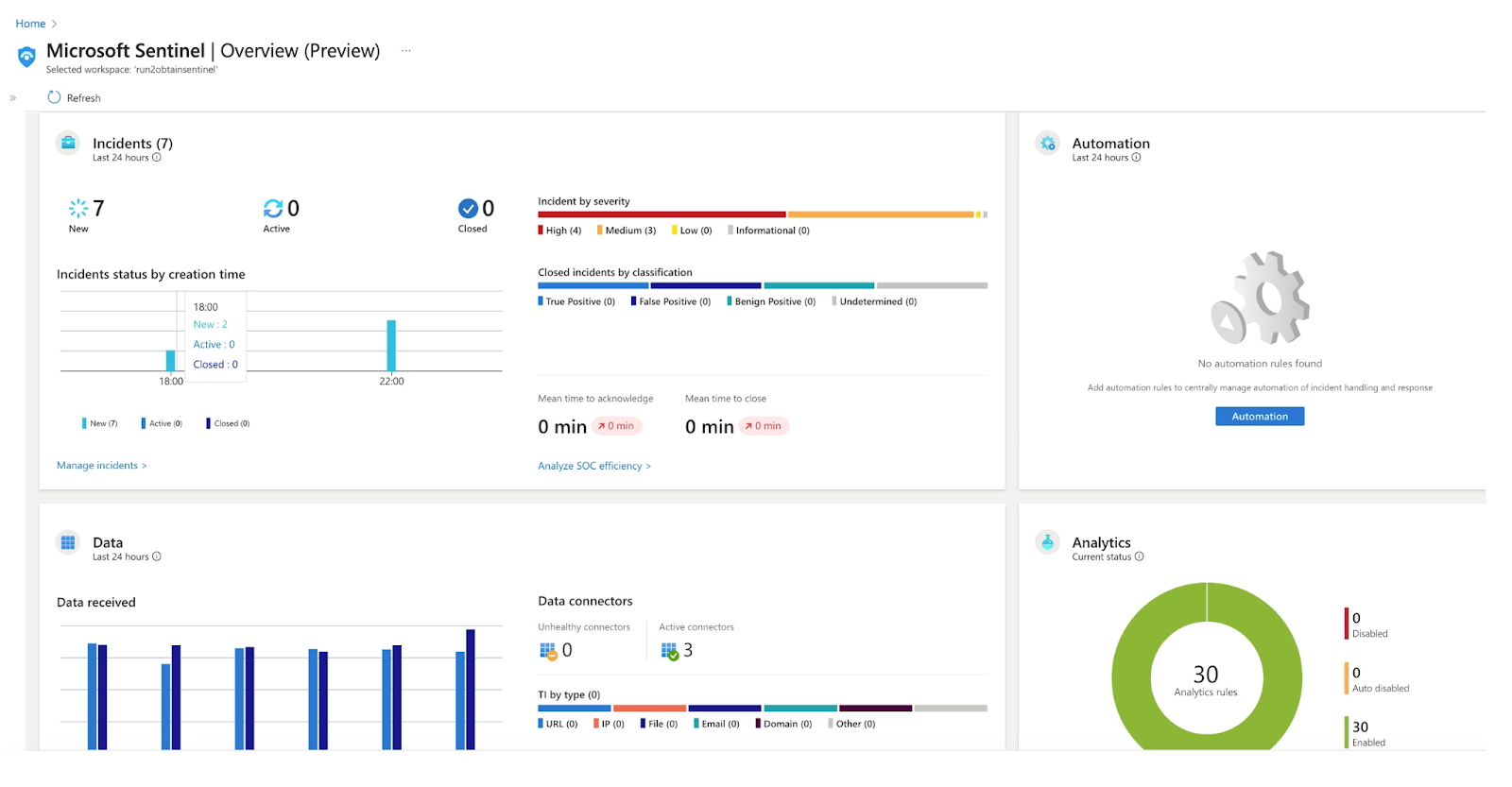
Sentinel is equipped with detection rules, expressed in Kusto Query Language (KQL), which provide powerful search capabilities over logs, such as Azure Activity Logs. However, Security Operations Center (SOC) teams often experience alert fatigue, making contextual rule tuning crucial to overcome this challenge. Detection engineers typically leverage environmental requirements and other contextual insights to customize KQL queries for optimal alerting, a process that is integral to the effective functioning of Sentinel.
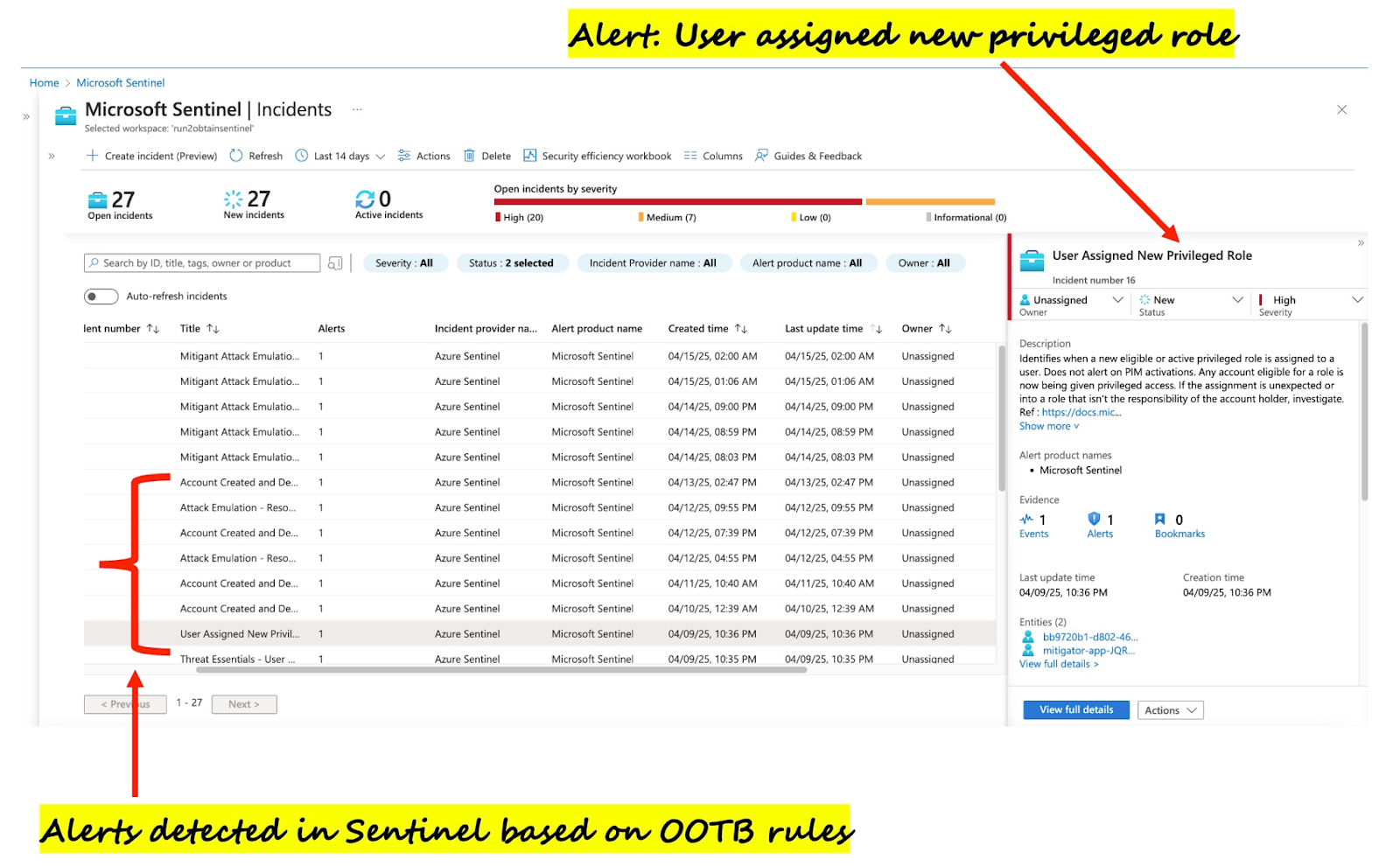
Sentinel ships with some detection rules (analytic rules) available in the Content Hub, which can be used as templates for creating more rules. Several alerts are seen in the Incidents panel following the execution of emulated attacks with Mitigant CAE, e.g., the alert displayed in the image is a “User Assigned New Privileged Role” alert.
Mitigant Cloud Attack Emulation (CAE) Overview
Mitigant CAE, a cloud-native, agentless adversary emulation platform, is at the forefront of the cybersecurity category of Adversarial Exposure Validation (AEV), recently introduced by Gartner. AEV combines Breach & Attack Simulation, Automated Red Teaming, and Automated Penetration Testing into a single product, enabling security teams to address the dynamic threat landscape swiftly. With Mitigant CAE, security teams can safely and efficiently emulate sophisticated attacks, mirroring the Tactics, Techniques, and Procedures (TTPs) of real-world threat actors, a unique feature that sets it apart in the industry.
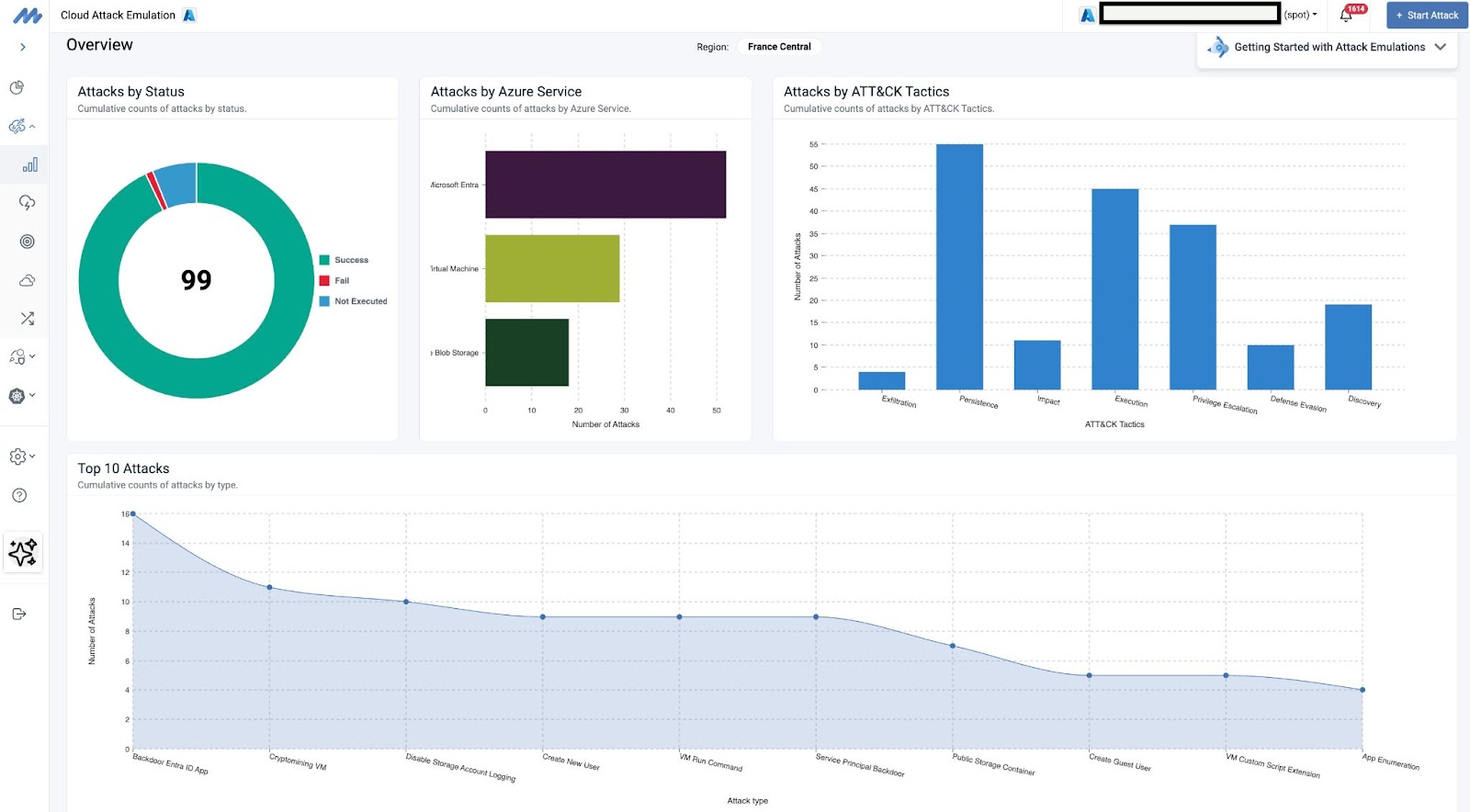
Mitigant CAE aligns with industry-standard frameworks like MITRE ATT&CK and MITRE ATLAS, providing a structured approach to simulating diverse attack scenarios. By integrating Cyber Threat Intelligence, CAE can emulate specific threat actor TTPs, giving security teams a realistic understanding of how their cloud environment might be targeted. Furthermore, Mitigant CAE offers a powerful API for seamless integration into Detection-as-Code via its Attack-as-Code feature, enabling automated and repeatable attack simulations. Attacks can also be easily launched from the Mitigant user interface, either immediately or scheduled for a later time, offering unparalleled flexibility.
Combining Sentinel and Mitigant CAE
While Sentinel provides the detection capabilities, how do you ensure your defenses are truly effective against the latest attack techniques? This is where Mitigant Cloud Attack Emulation (CAE) comes into play. Mitigant CAE is an industry-leading, agentless adversary emulation platform designed explicitly for cloud-native infrastructure. It allows security teams to safely and efficiently emulate sophisticated attacks, mirroring the tactics, techniques, and procedures (TTPs) of real-world threat actors.
The true power of this ultimate combo lies in the seamless integration between Sentinel and Mitigant CAE. Sentinel's detection rules, expressed in Kusto Query Language (KQL), provide robust capabilities for searching and analyzing logs, such as Azure Activity Logs. However, SOC teams often grapple with alert fatigue, making rule tuning an imperative duty.
While Sentinel provides some Out-of-the-Box (OOTB) detection rules, such as "User Assigned New Privileged Role," the number of these OOTB rules (fewer than 30) and often insufficient for comprehensive attack detection. This leaves critical gaps in an organization's defense. For instance, there is no OOTB Sentinel rule for detecting malicious VM disk exfiltration, an attack that can lead to significant data breaches. Similarly, detecting the spawning of rogue VMs for activities like crypto-mining often requires custom detection logic.
Expectedly, SOC teams are responsible for adding detection rules; however, these rules must be tested for effectiveness. This is an iterative process and could lead to alert fatigue and false positives if not handled well. This is where the ultimate combo shines, providing a comprehensive approach to detection and response.
Let's consider a few practical examples where Mitgant CAE is used to identify attack opportunities and security gaps in an Azure subscription. We demonstrate how we utilize KQL to create detection rules for the remediation of these findings.
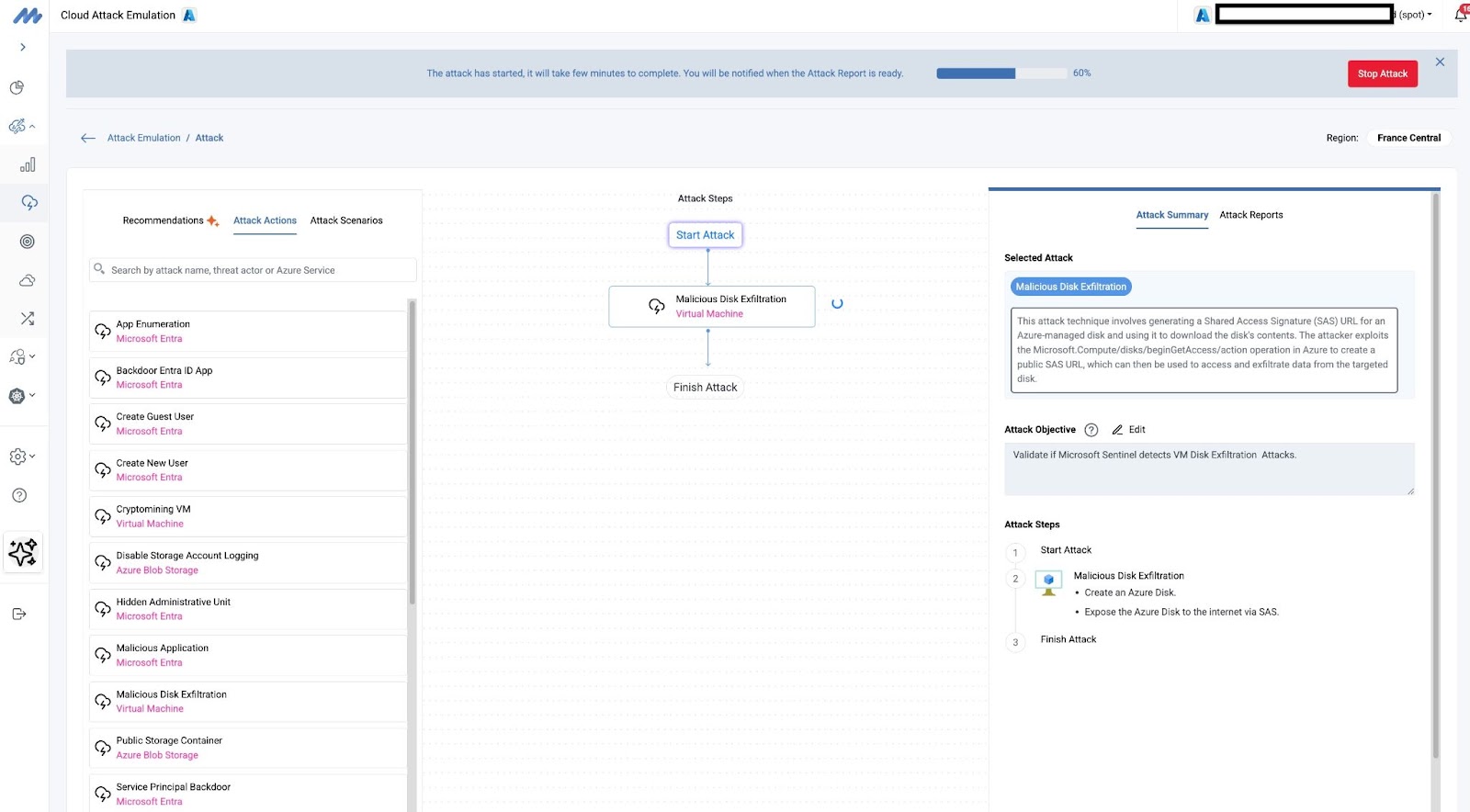
Example Scenario 01: Detecting “VM Disk Exfiltration” Attack
An attack vector commonly used by attackers is VM “disk exfiltration”, which allows them to share the VM disk using shareable links implemented via Azure Shared Access Signature. This attack falls under MITRE ATT&CK Technique T1048 (Exfiltration Over Web Service). This technique is leveraged by attackers to exfiltrate VM disksto locations within or outside the Azure cloud for further malicious examination. In reality, this attack abuses the disk sharing feature provided for benign use cases, e.g., backups.
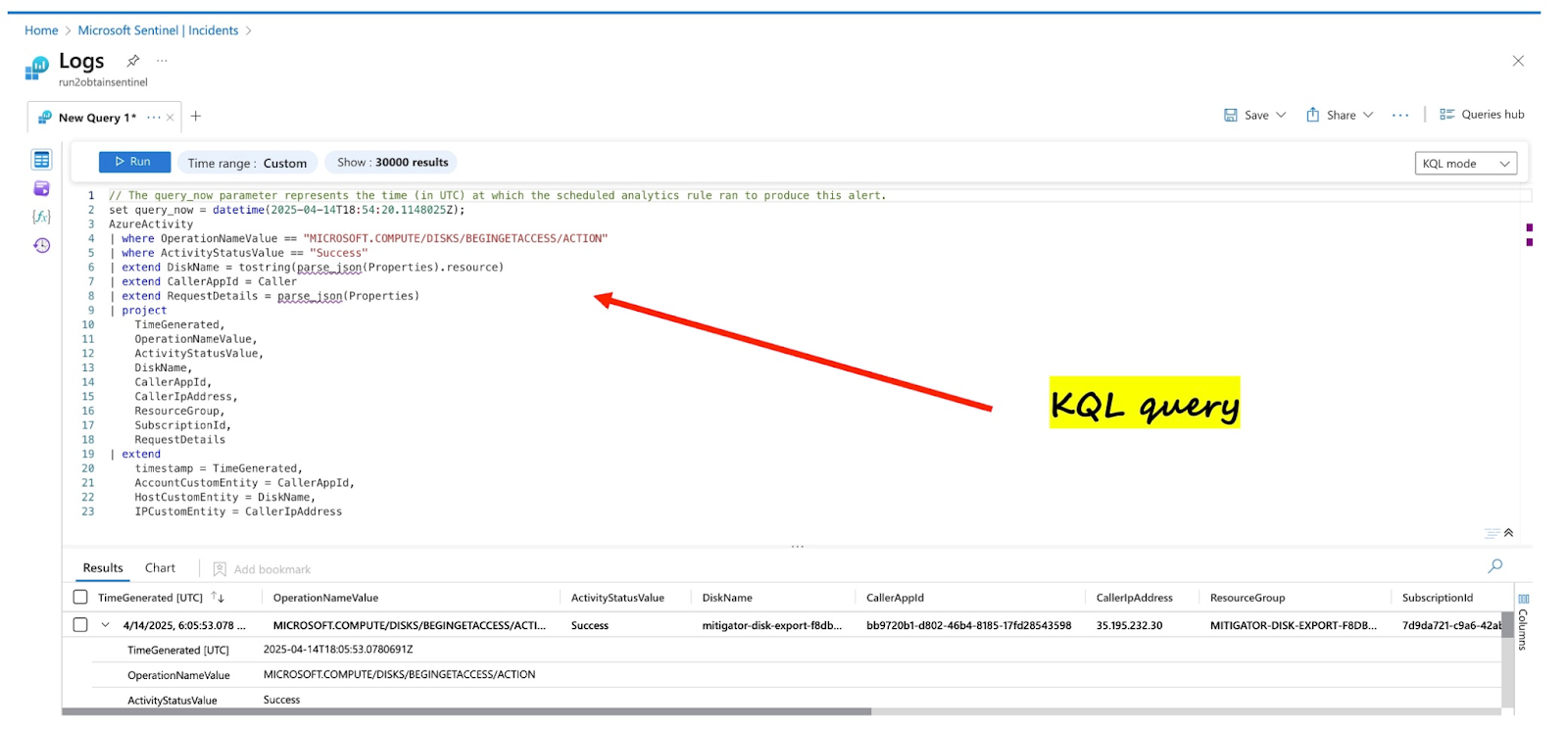
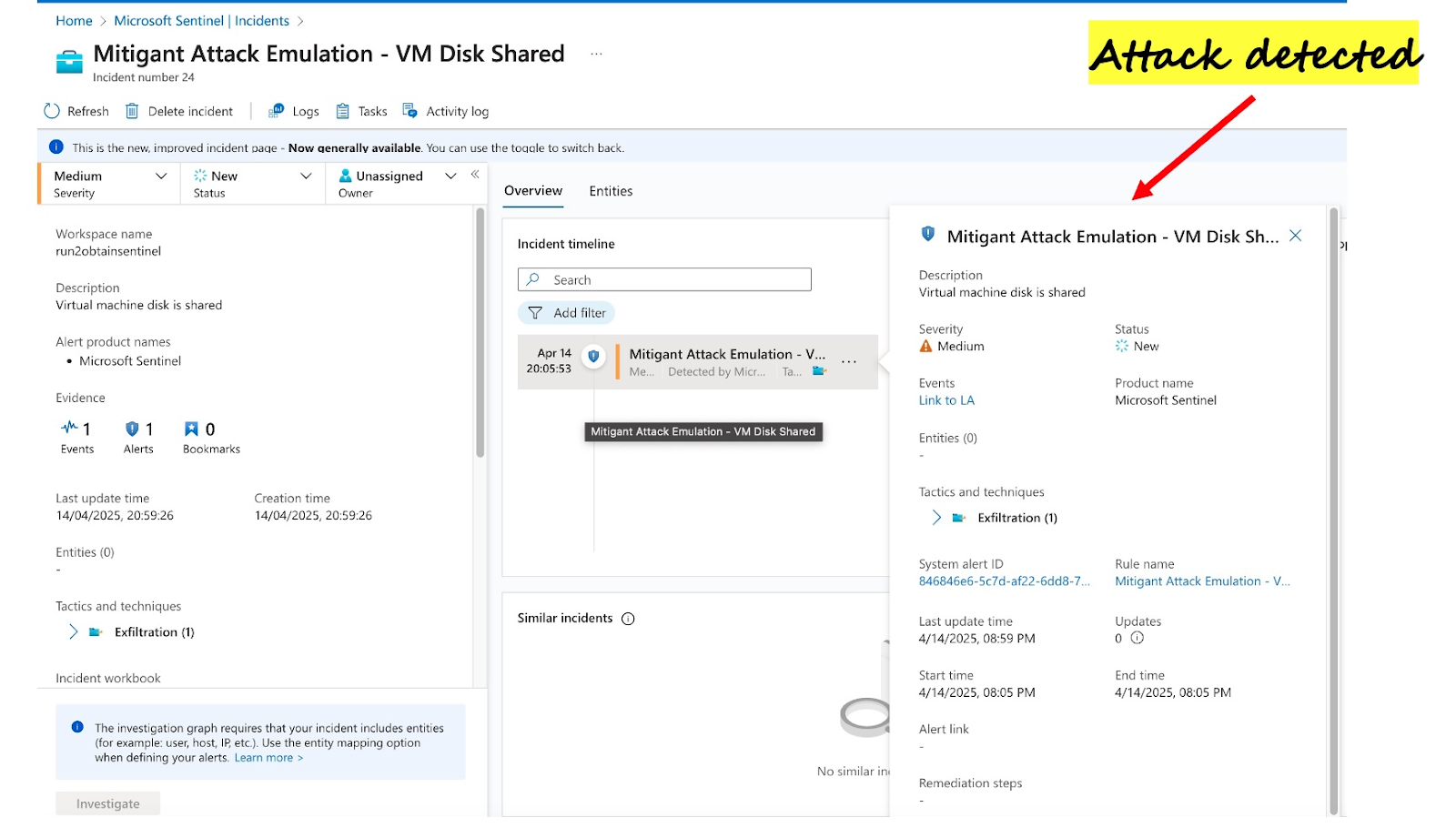
Interestingly, there is no analytics rule for detecting this attack in the default Sentinel content pack; therefore, we implemented a corresponding rule using KQL for this. As seen in Figure 06, the rule identifies the attack accurately (executed with Mitigant CAE - Figure 05). This is also visible in the Sentinel dashboard, as shown in Figure 07.
Example Scenario 02: Detecting Malicious “VM Creation” Events
Sophisticated cybercriminals, e.g., APTs, are more likely to create VMs as this gives them space to stay undetected and coordinate attacks to navigate deeper into the compromised environment. These rogue VMs provide a shelter that could serve as a command and control points for attackers.
Rogue VMs are commonly used by attackers to import exploits from their base into the compromised environment. Furthermore, attackers can easily monitor the compromised environment closely from the rogue VMs, allowing a clearer understanding of the victim network architecture, defensive measures, etc. Attackers used this technique in the recent attack against the MITRE Research Centre, even naming the rogue VMs according to the internal naming convention to further evade detection.
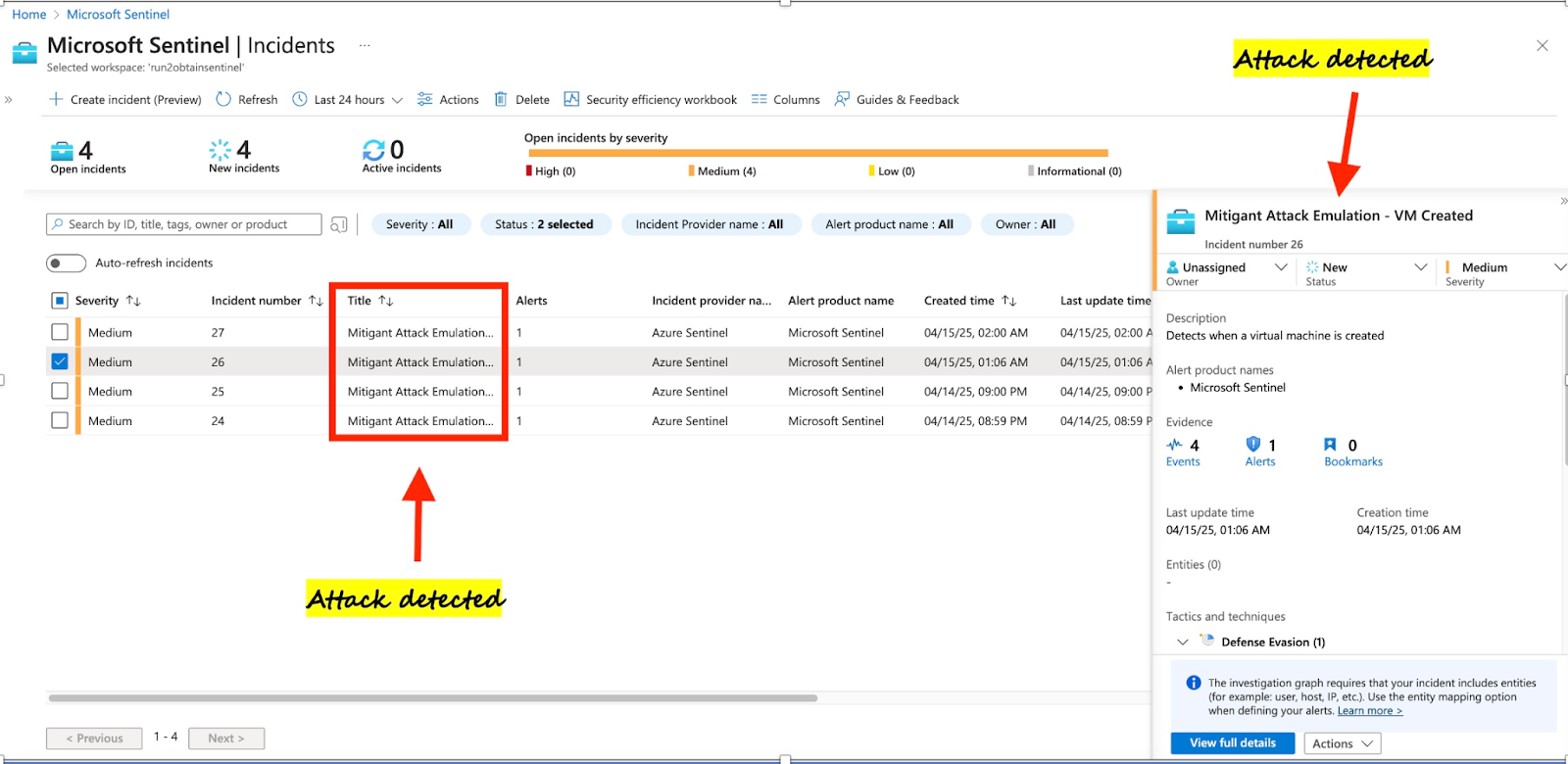
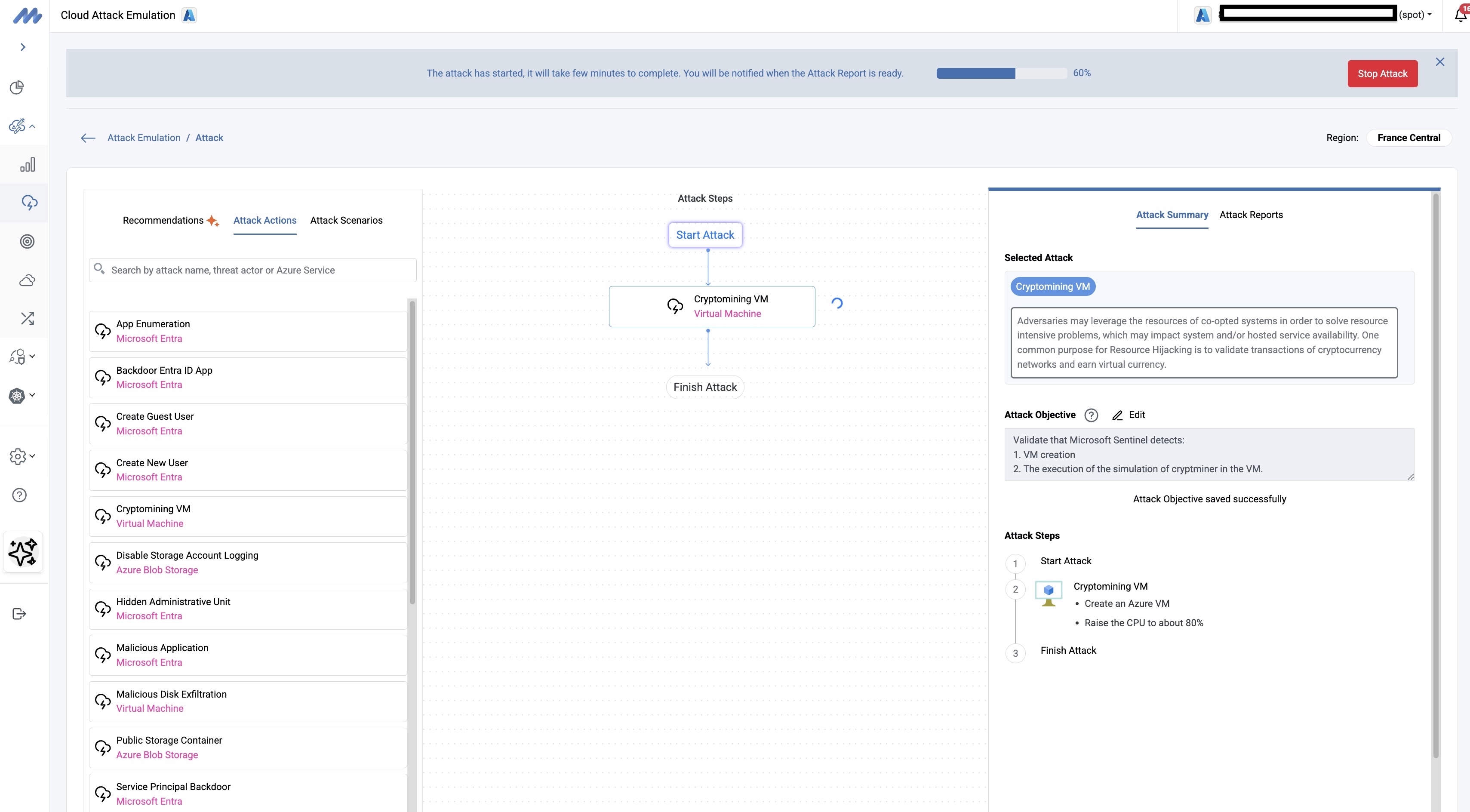
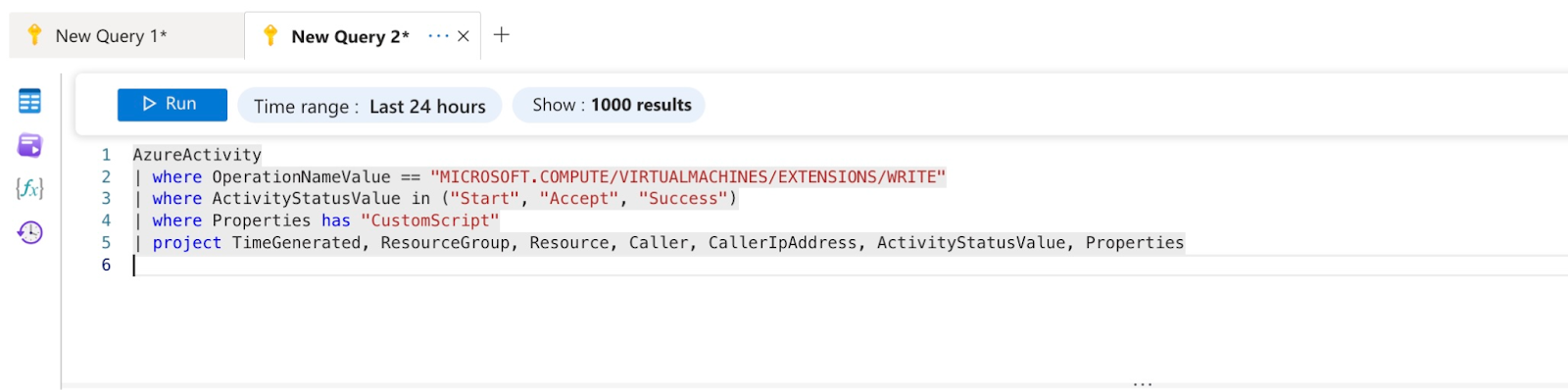
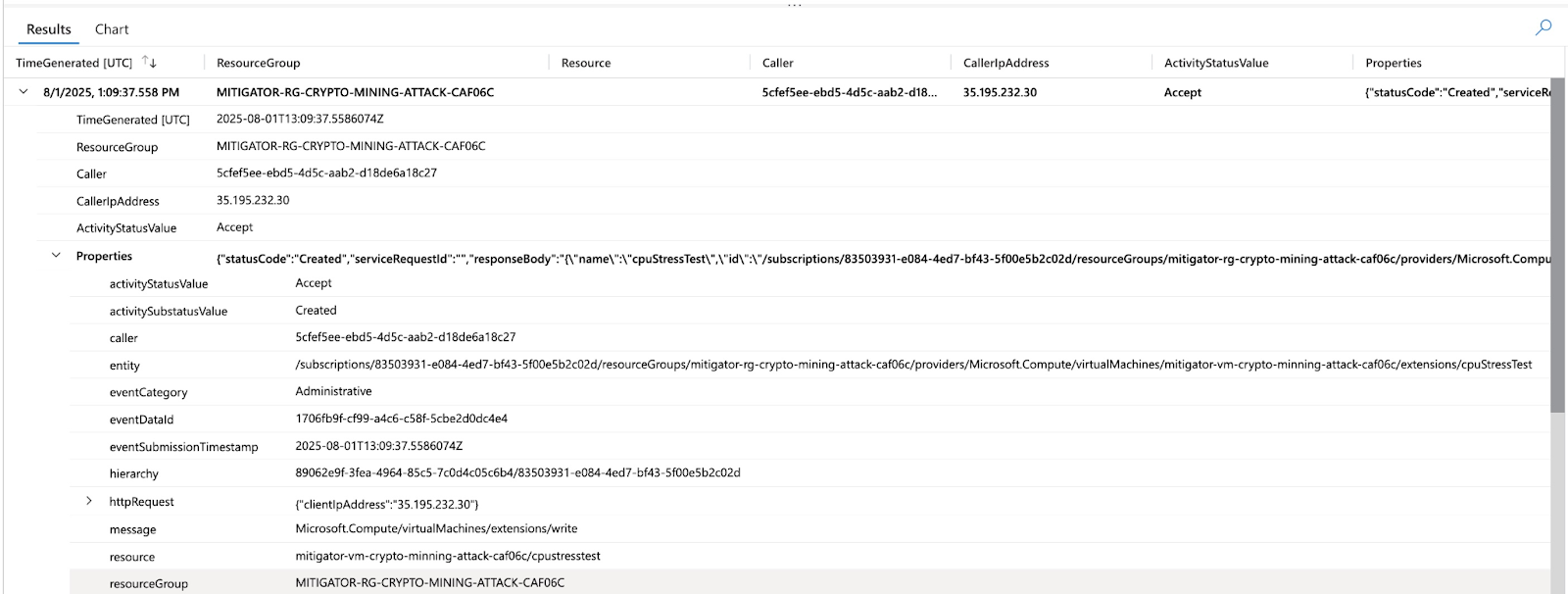
However, most security teams tend to dismiss VM Creation events as they create a lot of noise; most VM creation events are routine. Rather than rejecting these events, a wiser approach is to implement clever detection rules that can sift out VM creation events that deviate from the baseline behaviour. Figure 08 shows the execution of the cryptomining attack using Mitigant CAE; a new VM is spun up to conduct the attack, which includes the execution of a CLI command using the Windows Script Extension. This attack is however detected due to the rule we implemented in Sentinel using the KQL in Figure 10. The alert indicating the attack is displayed in the Sentinel dashboard - Figure 09.
Combining Sentinel with Mitigant CAE: Advantages
There are several advantages security teams can derive by combining Sentinel with Mitigant CAE. Let’s discuss some of these advantages.
Optimize Detection Engineering Efforts
The threat landscape evolves rapidly, and the analytics rules provided in the Sentinel content pack are grossly insufficient to protect organizations. Ultimately, SOC teams, especially detection engineers, need to build rules that contextually fit their use cases. Such rules need to be tested for efficacy, and this can be achieved using Mitigant CAE.
By providing a structured and automated way to test and validate detection logic, the combo optimizes the entire detection engineering lifecycle. Security engineers can quickly iterate on their KQL queries, ensuring they are practical and efficient in identifying threats. Mitigant CAE can be leveraged to enhance and mature detection engineering capabilities by integrating it into the Detection Engineering Development Lifecycle.
Furthermore, by emulating specific attacks that are not covered by OOTB rules (like VM disk exfiltration or rogue VM detection), security teams can immediately identify gaps in their Sentinel detections. They can then create and fine-tune custom KQL queries to effectively detect these previously elusive threats. Mitigant CAE provides the real-world attack data needed to validate and optimize these custom rules, ensuring they generate accurate and actionable alerts.
Reduce Alert Fatigue
By continuously validating and refining detection rules using CAE, SOC teams can significantly reduce the number of false positives and irrelevant alerts. This allows them to focus on genuine threats, leading to a reduction in alert fatigue and an increase in operational efficiency.
Streamlined Red/Purple Teaming
The Azure Security Controls recommend regular red/purple teaming exercises, including penetration tests (ASB 11.1). Mitigant CAE simplifies this recommendation by eliminating the need to manage complex attack scripts, enabling red/purple teams (including engineering teams with no deep technical offensive expertise) to launch sophisticated attacks with ease. Furthermore, Mitigant CAE provides evidence data for further analysis and remediation instructions to fix identified gaps.
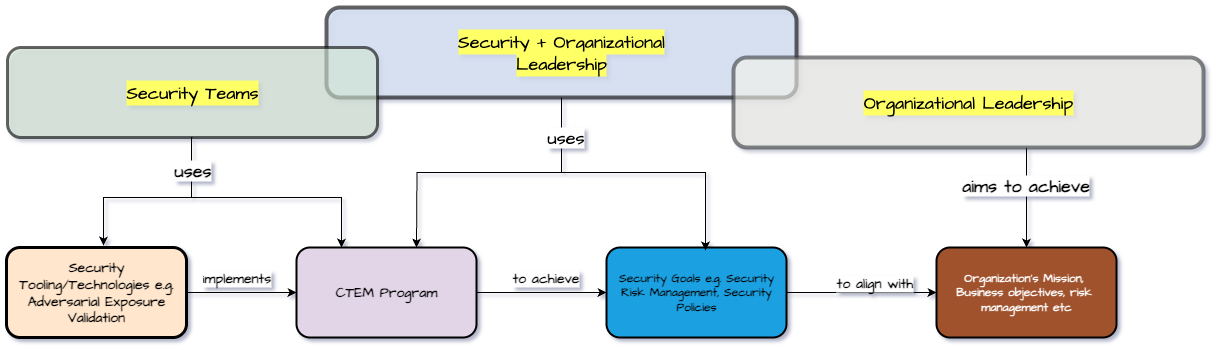
Operationalization of CTEM & Threat-Informed Defense
Many security teams waste precious time chasing vulnerabilities based on CVSS scores and other vanity metrics. However, such vulnerabilities are too much to fix and often result in limited security outcomes. A more efficient approach consists of leveraging CTEM and Threat-Informed Defense. CTEM has a five-step process; have a look at the detailed explanation of these steps in our previous blog post. Most importantly, Mitigant CAE caters to three steps: prioritization, validation, and mobilization. Furthermore, Mitigant CAE empowers operationalization of Threat-Informed Defense; SOC teams can easily validate the efficacy of defensive measures, including Cyber Threat Intelligence.
Supercharge Threat Hunting
Mitigant CAE empowers threat hunters by providing a mechanism to craft and validate hypotheses easily. By emulating specific attack TTPs, hunters can actively search for evidence of these attacks within their Sentinel logs, validating their hunting queries and improving their ability to uncover stealthy threats.
Enable Effective Cloud Detection & Response
The integration of Microsoft Azure Sentinel and Mitigant CAE represents a paradigm shift in cloud security. It moves beyond reactive incident response to a proactive security posture, enabling organizations to validate their defenses against evolving threats continuously. By combining Sentinel's robust SIEM capabilities with Mitigant CAE's sophisticated attack emulation, security teams can enhance security effectiveness in several ways.
This ultimate combo offers a powerful solution for maturing your detection engineering capabilities and ultimately, safeguarding your critical cloud assets. Don't just detect threats, actively validate your ability to do so. Sign up for a free trial of Mitigant CAE today and experience the ultimate combo for cloud security.






.png)
