Feature Release: Multi-Cloud Attack Emulation


We are excited to announce several features recently added to the Mitigant Cloud Security Platform. Multi-cloud attack emulation is the most exciting feature, enabling hassle-free orchestration of attacks across AWS and Azure. Other features include evidence collection and detection logic for Azure Cloud Attack Emulation (CAE), support for Azure Tenant-level onboarding, and support for DORA and NIS2 compliance.
Multi-Cloud Attacks
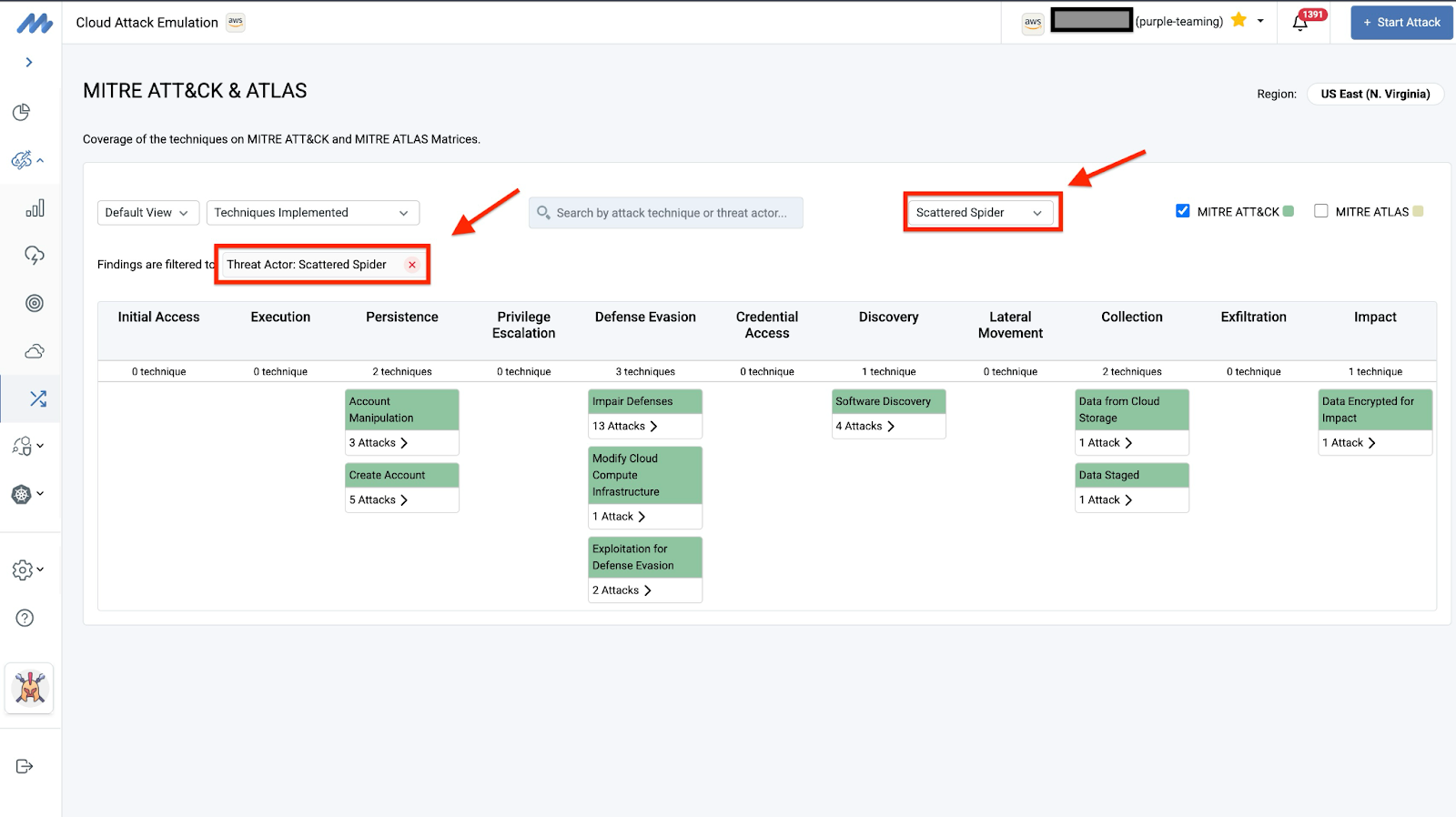
Multi-cloud attacks are the new norm; attackers increasingly launch attacks that span across two or more cloud service provider platforms. These attacks, often implemented by APTs and threat groups like the infamous Scattered Spider, use several known MITRE ATT&CK techniques. However, despite public knowledge of these techniques, defensive visibility remains nonexistent, thereby making attack detection and countermeasures even more challenging.
The truth is that most cloud defensive tools, particularly those focused on detection and response, are still entrenched in the single-cloud era. While these tools may succeed in addressing single-cloud attacks, they fail to detect multi-cloud attacks. Furthermore, the current state of detection engineering and analytics is oblivious to the multi-cloud dimension. Some detection rules are beginning to correlate similar events into clusters, providing clearer visibility; however, these efforts still focus on single-cloud security events.
The newly released multi-cloud attack feature aims to initiate efforts that address the challenges of detecting multi-cloud attacks. The feature is built on Mitigant Cloud Attack Emulation (CAE), a unified and powerful platform that enables defenders to comprehend multi-cloud attacks and develop effective countermeasures across multiple cloud service platforms.
Let's examine one of the available multi-cloud attack scenarios: Backdoor Data Exfiltration. This multi-cloud attack scenario consists of three attack actions:
- New Privileged User: This initial attack action establishes a critical requirement for the subsequent attacks. An AWS IAM User is created and assigned privileges to read and write secrets to the AWS Secret Manager by attaching the managed policy SecretsManagerReadWrite to the IAM User. Next, the user creates a few secrets, which are then stored in the Secret Manager. The access key and secrets for this new IAM user are then configured as environment variables in an Azure VM in the target Azure subscription.
- Compromised Windows VM: This attack initiates a more central aspect of the attack. The credentials previously implanted in the Azure VM are retrieved and examined, as potential attackers would do to gain a clear view of attack possibilities. Here the attack takes advantage of the Windows Customs Script Extension to execute malicious commands as described in MITRE ATT&CK technique T1059.009 (Command and Scripting Interpreter: Cloud API).
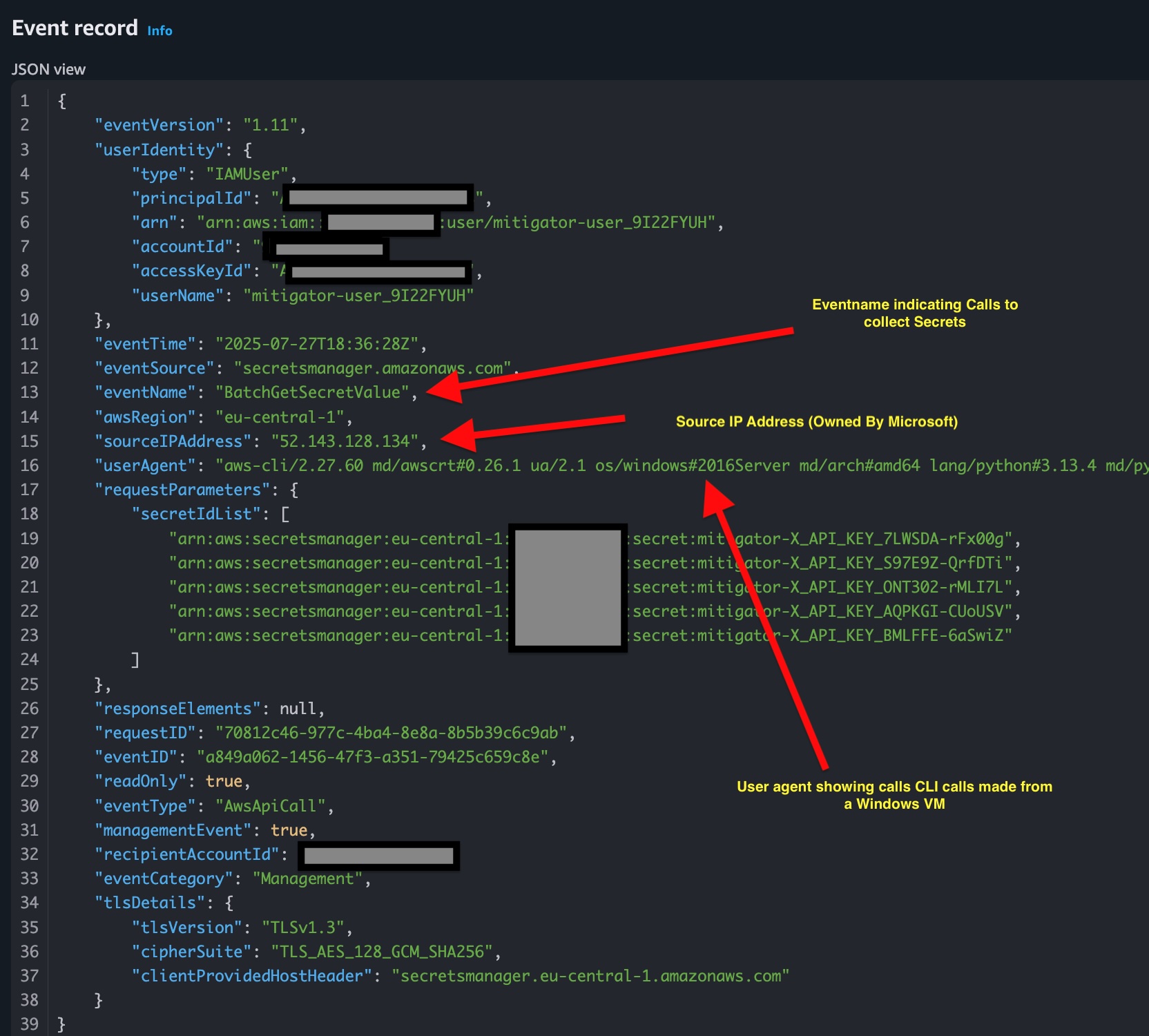
- Malicious Secrets Retrieval: In this step, the attack proceeds to move laterally into the AWS account whose credentials were previously retrieved in the Azure VM demonstrating the attack technique T1555.006 (Credential from Password Stores: Cloud Secrets Management Stores). The secrets stored in the AWS Secret Manager are then retrieved for further attacks. Note that there are different variants of this attack especially for AWS Secrets Manager, we discussed these variants in previous blog post, have a look here.
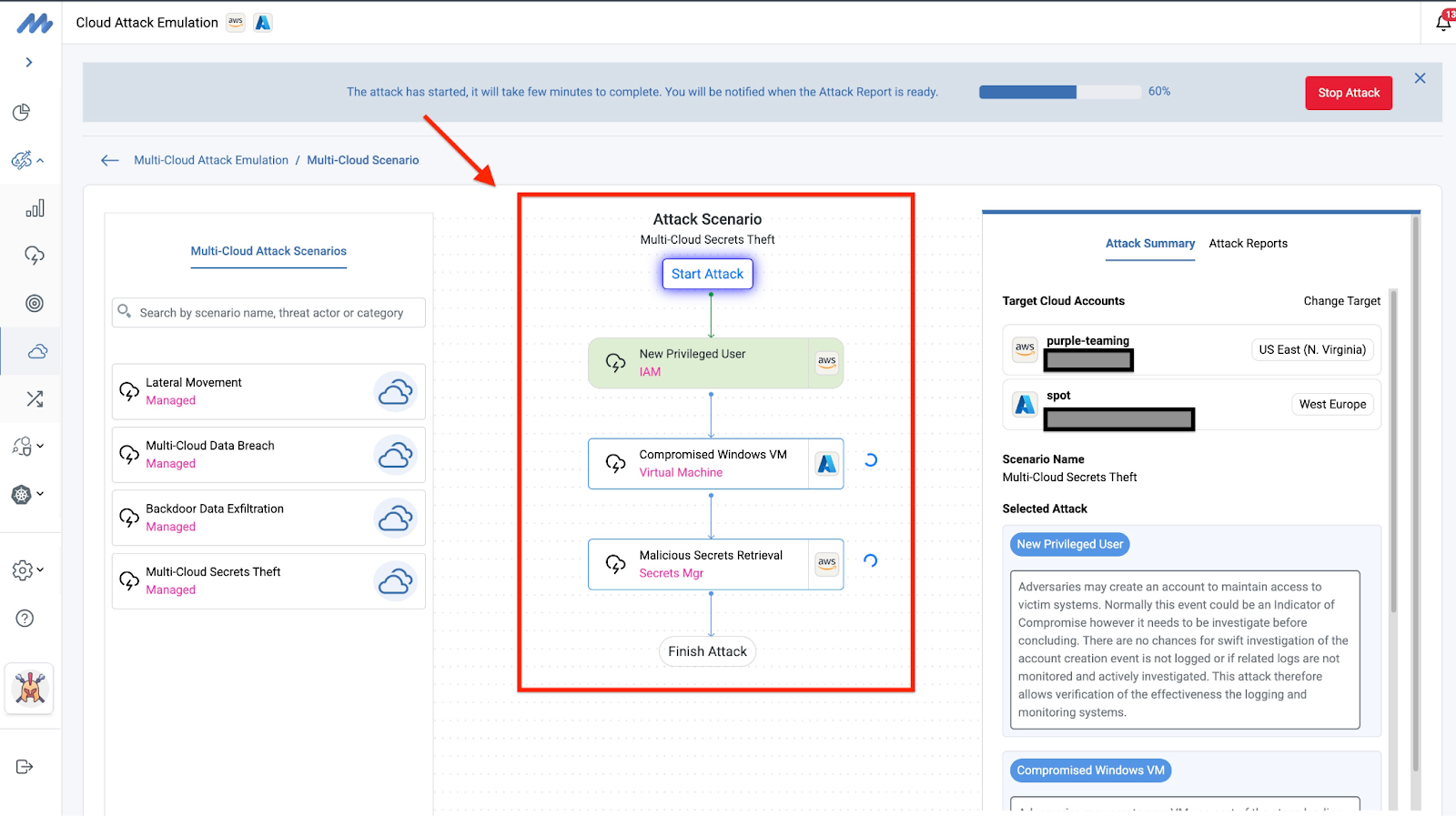
Notably, the first attack sets the stage for the attack emulation, while the second and third attacks are the most interesting steps of the multi-cloud attack scenario. All the resources created are thereafter destroyed after 5 minutes; this is a standard process in Mitigant CAE. The corresponding attack telemetry is also collected and provided. In a future blog post, a detailed analysis of multi-cloud attack scenarios will be provided.
Azure CAE Updates
CAE for Azure was released in March of this year, and since then, several features have been added, similar to those in CAE for AWS. Let's examine two key features that have been recently added: evidence collection and detection logic.
Evidence Collection
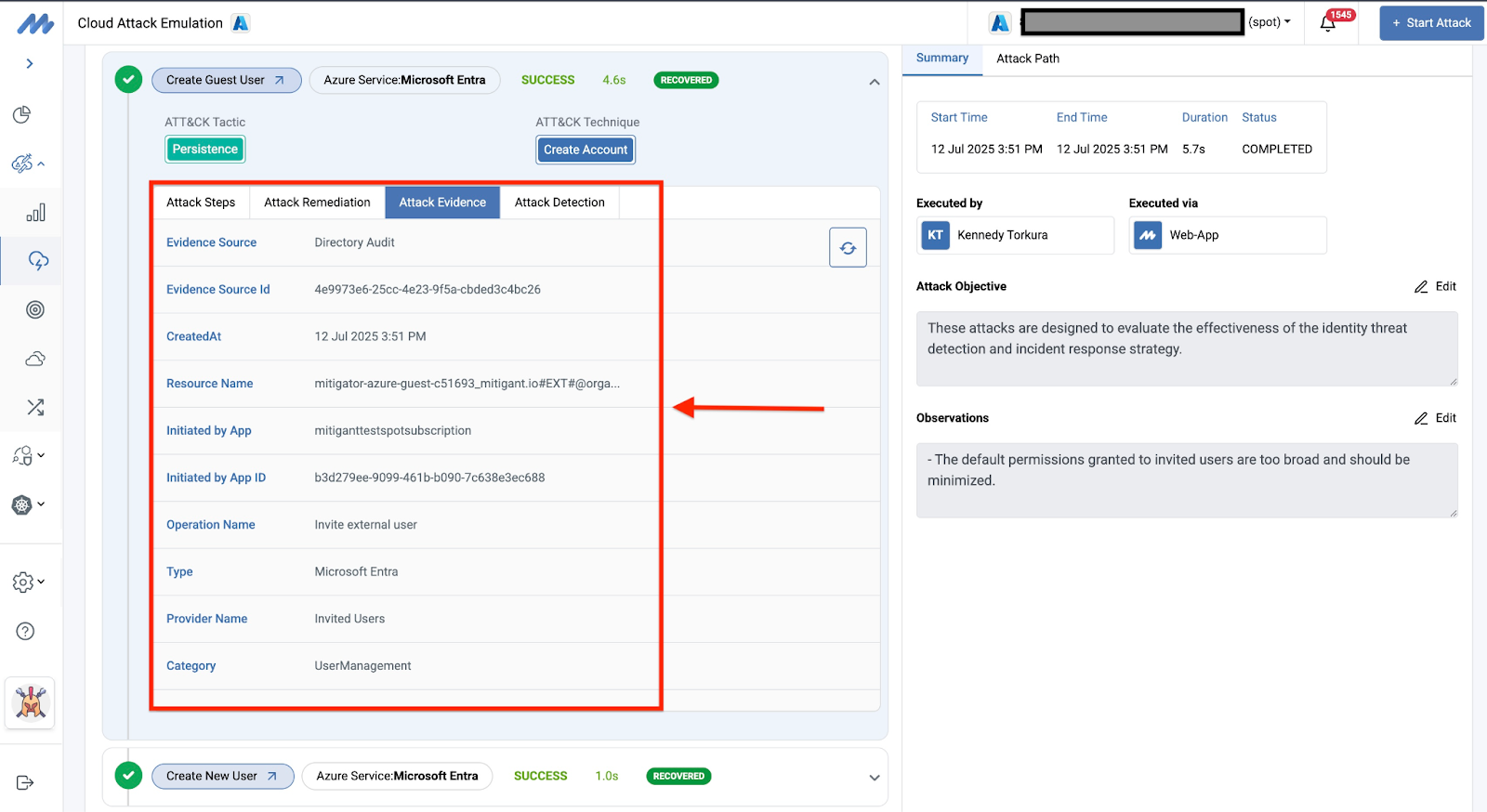
Attack telemetry is vital for understanding attacker behaviour and subsequently implementing effective countermeasures. Consequently, the logs generated due to emulated attacks are collected and displayed to users. These logs are collected from Azure Activity Logs and Azure Audit Logs (specifically for Entra ID attacks). The logs provide relevant information that can be utilized by SOC teams for further analysis, investigations, and other purposes.
Sigma Detection Rules
Detection logic is a central aspect of every threat detection system; they are used to define the essential properties that can be extracted from event logs to precisely flag an event as malicious. To support our goal of enabling SOC teams to be agile and productive, every attack report includes corresponding detection logic in Sigma format. With this logic, defenders can easily close detected gaps by applying the Sigma rule directly or converting it to the corresponding format based on the specific threat detection vendor.
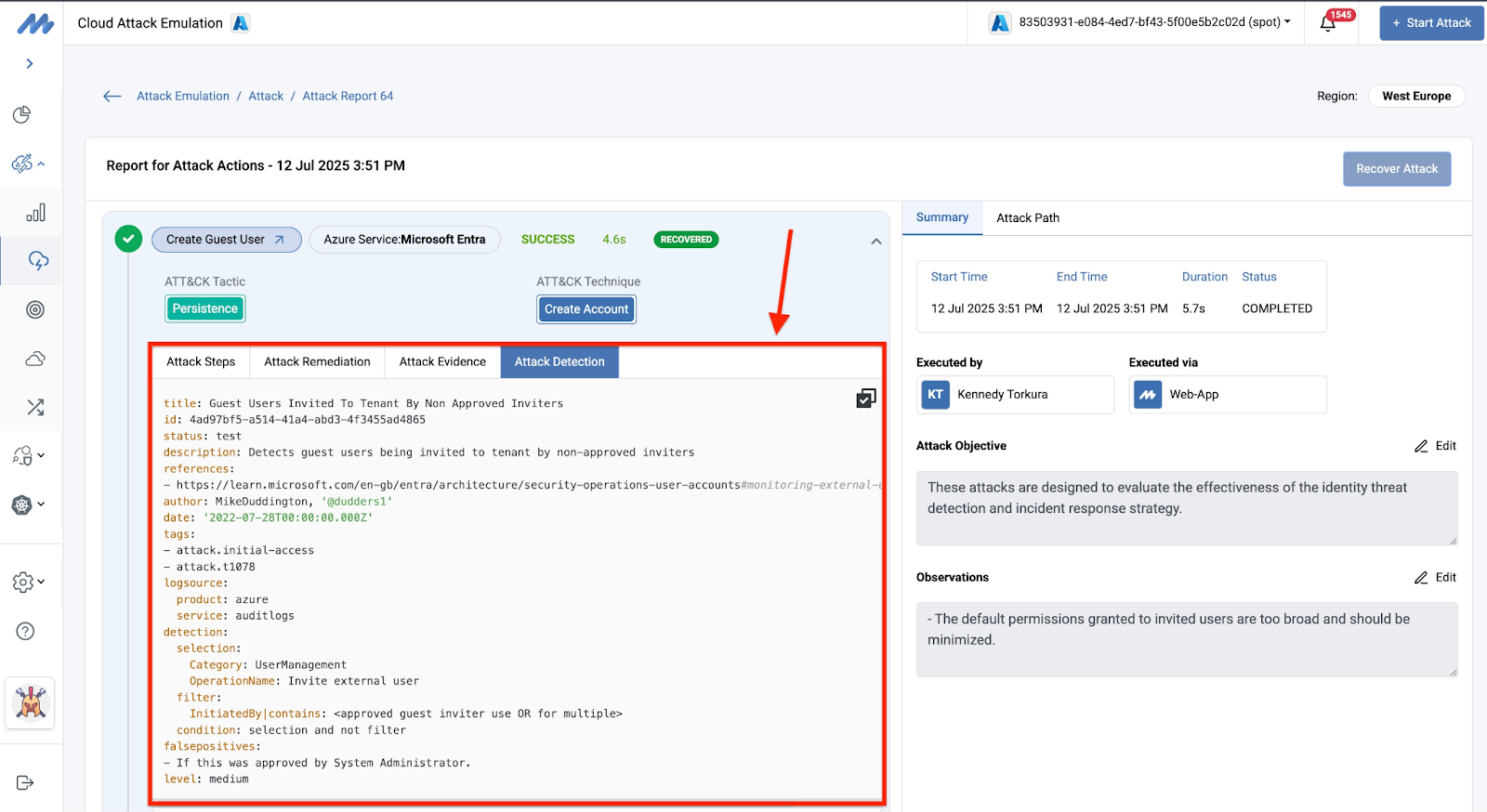
Support for NIS2 and DORA Assessments
Most organizations in the European Union are obliged to support at least one of the recent regulations: the EU Network and Information Security (NIS2) Directive and the Digital Operational Resilience Act (DORA). While cloud service providers could be attested for both NIS2 and DORA, organizations using these services must ensure that their cloud environments are correctly aligned, as outlined in the Shared Responsibility Model. We previously thoroughly discussed NIS2, including affected organizations, requirements, and other relevant aspects. Check this page for details and watch our on-demand webinar.
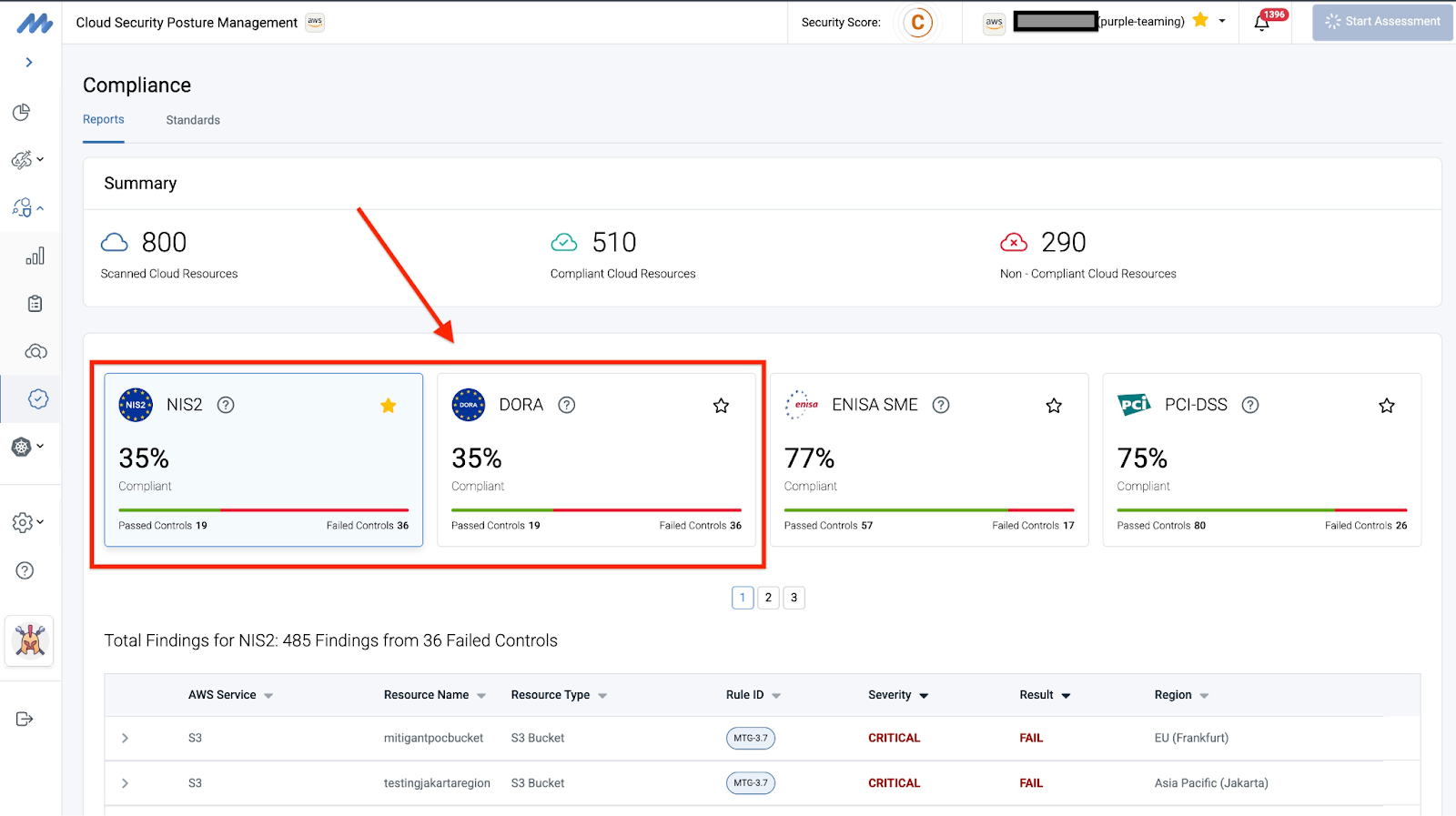
Mitigant CSPM automates the process of checking the NIS2 and DORA compliance level of cloud resources on AWS and Azure. Reports are provided in several formats, including PDF, JSON, and CSV. Furthermore, affected organizations can leverage Mitigant CAE for Threat-Led Penetration Testing, which is one of the requirements introduced under DORA. It requires that affected organizations run real-life attack scenarios based on specific threat actors as specified in Cyber Threat Intelligence Reports. Mitigant CAE has over 150 attacks, all mapped to MITRE ATT&CK and MITRE ATLAS frameworks and appropriately tagged with the threat actors that are reported to use these attacks against organizations, e.g., APT29.
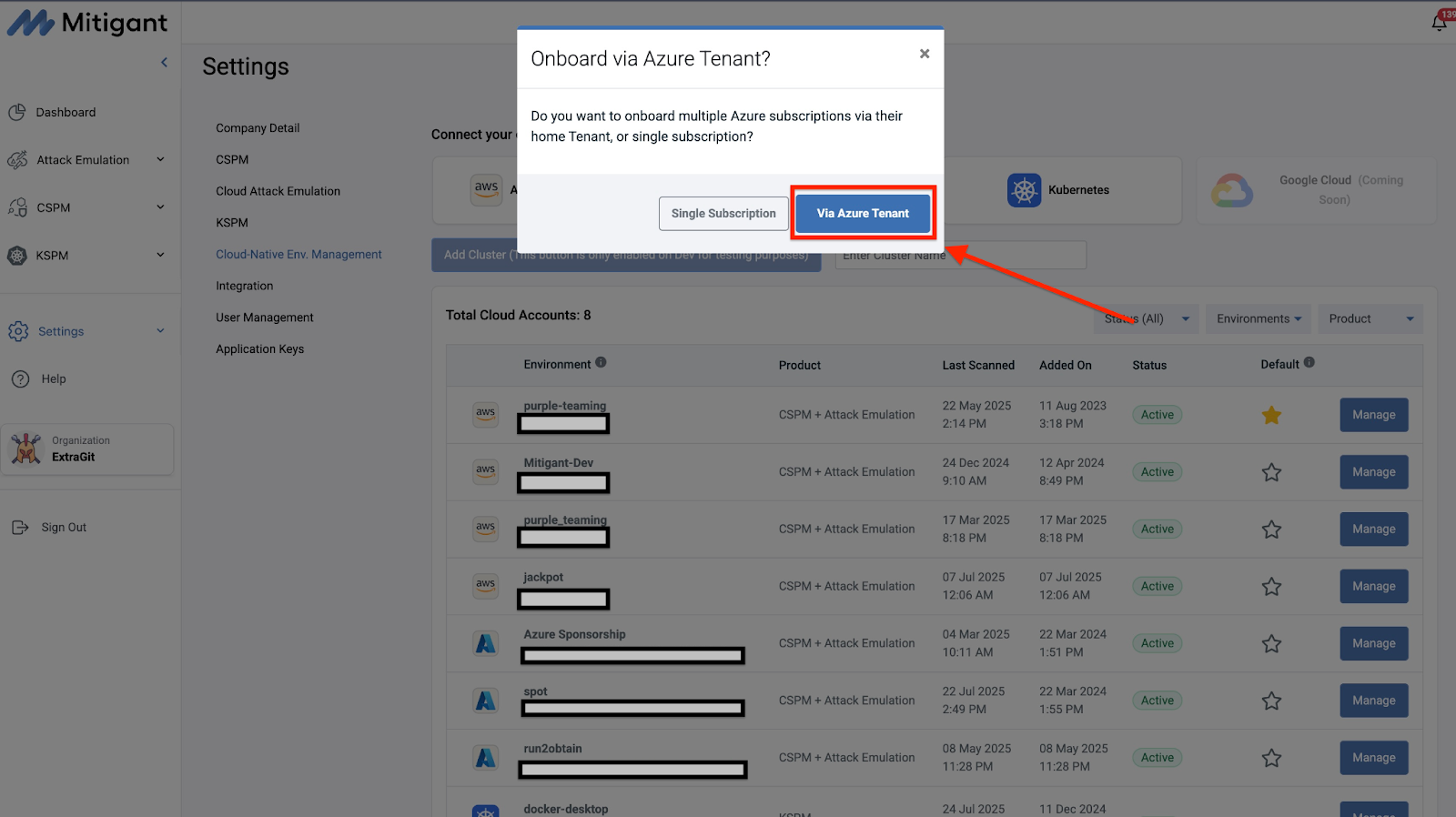
Support for Azure Tenant
Many organizations have multiple subscriptions grouped under the Azure tenant construct. In such scenarios, onboarding multiple accounts can be quite a chore if done completely manually. This chore is eliminated with the recently released support for Tenant-Level onboarding; all subscriptions under a Tenant are automatically discovered during onboarding and subsequently disabled, allowing users to add them easily. In most cases, this is a one-click operation, as the service principal used for onboarding typically has sufficient privileges to access other subscriptions. We previously added similar support for AWS Organizations, enabling the easy onboarding and assessment of multiple AWS accounts through organizational-level management.
Securing Kubernetes Clusters on Hetzner & SysEleven
Several organizations in Germany and Europe prefer to use managed Kubernetes services offered by European service providers. In Germany, SysEleven and Hetzner are well-known cloud service providers. Additionally, SysEleven provides MetaKube, a managed Kubernetes service very popular in the public sector. Similarly, while Hetzner does not offer a managed Kubernetes service, SySelf recently launched one on top of Hetzner.
Mitigant has partnered with SysEleven and Syself to provide high-quality security for their managed Kubernetes services. This partnership allows the use of Mitigant KSPM to provide value-added security for these managed Kubernetes services, especially as the compliance landscape in Europe continues to evolve.
Don’t Just Observe - Take Action Today!
The threat landscape is rapidly evolving, and attackers are increasingly using attacks that pivot from one cloud infrastructure to another; therefore, focusing solely on single-cloud attacks is grossly unrealistic and insufficient.
Defenders can address these multi-cloud attacks by emulating them within their own environments, allowing cloud security tools and processes to understand the workings of these attacks. This approach provides a foundational framework for hardening security and proactively thwarting multi-cloud attacks. In a future blog post, a deep dive into the analysis of multi-cloud attack scenarios will be provided; therefore, stay tuned.
Do not hesitate to reach out and sign up for a FREE Trial - https://www.mitigant.io/en/sign-up





.png)

