Cloud Attack Emulation 101: Shallow Waters


Cloud Attack Emulation 101: Shallow Waters
In Part I of this series, we provided foundational insights into Cloud Attack Emulation; the innovative application of adversary emulation to the cloud. In this second part, we're taking it a step further by wading into the shallow waters of how cloud attack emulation actually works, starting with the building blocks that enable empirical validation rather than vendor-claimed percentages. We then present fundamental aspects of Mitigant CAE that distinguish us from the market and consolidate this assertion by showing how organizations can leverage Mitigant CAE to fuse together two powerful industry strategies: Threat-Informed Defense and Continuous Threat Exposure Management (CTEM).
MITRE ATT&CK Coverage Fallacy: When Security Metrics Mislead
Security teams have become dangerously dependent on a single metric: MITRE ATT&CK coverage percentages. Vendors proudly tout "52% ATT&CK coverage" or "100% detection rates," while procurement teams make million-dollar decisions based on these numbers. Cyber insurance premiums rise and fall with coverage claims. But here's the uncomfortable truth backed by recent academic research: these percentages are creating a false sense of security that attackers are quietly exploiting
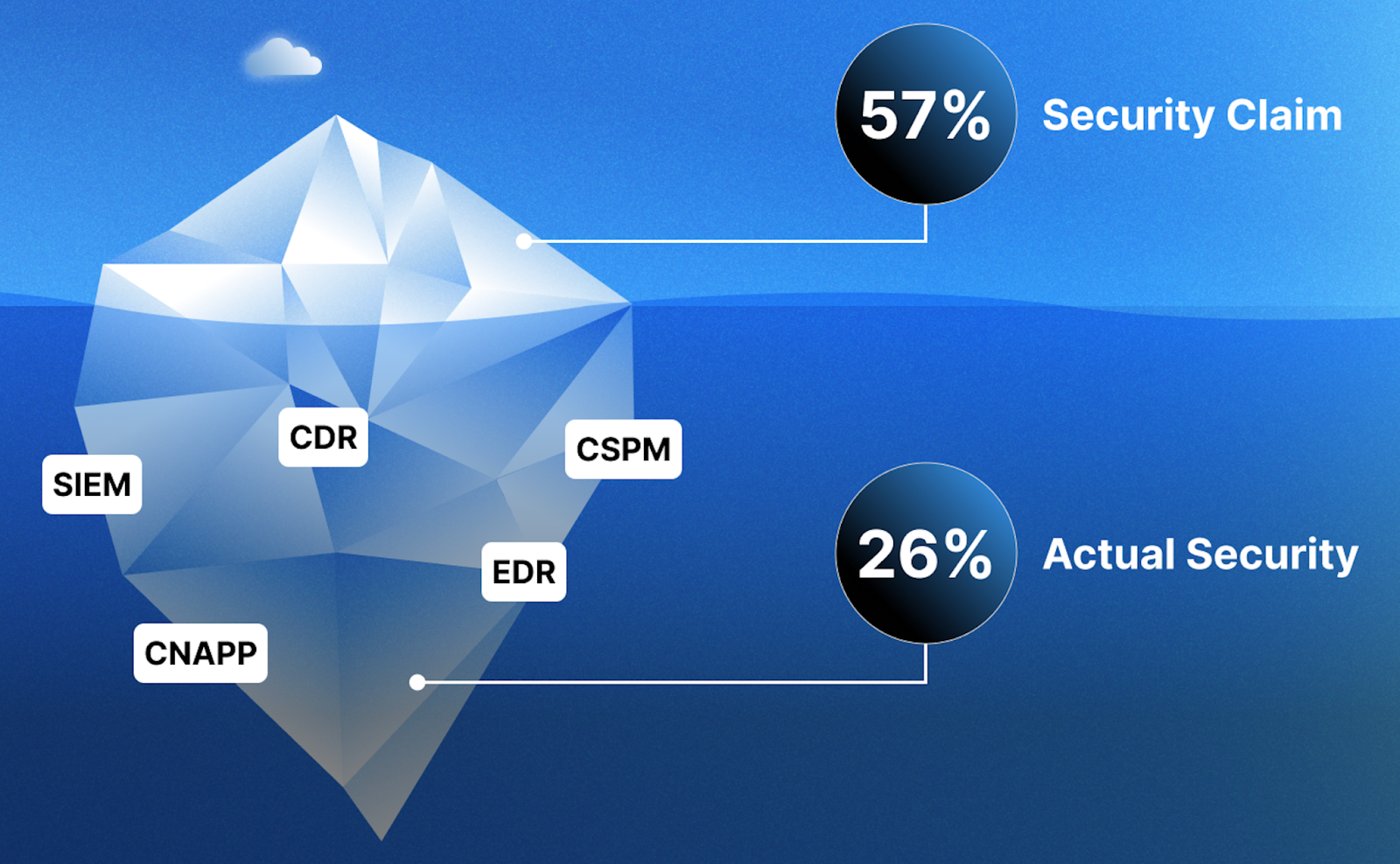
A comprehensive study analyzing three major endpoint detection products alongside open-source detection rules uncovered a troubling reality gap. When researchers filtered for only high-severity rules (the detections that actually matter during critical attacks), coverage percentages plummeted from 48-55% to just 25-26%.
The implications extend far beyond academic curiosity; organizations are making risk decisions based on incomplete information, building security strategies on foundations that shift depending on which vendor's perspective they adopt. Nearly 28% of ATT&CK techniques had no detection rules in any of the products examined, while another 40% relied on methods prone to high false positives.
This is where Mitigant Cloud Attack Emulation (CAE) fundamentally differs, rather than claiming coverage based on theoretical detection rules, Mitigant CAE validates the effectiveness of these security tools when deployed in cloud environments. We move organizations from the fallacy of coverage claims to the reality of security effectivenss; empirical validation that shows exactly which attacks succeed, which defenses hold, and where the gaps truly exist.
Mitigant Attack Primitives
Cloud attack emulation starts with modular building blocks; atomic attack actions and multi-step scenarios that combine flexibility with realism, enabling security teams to test everything from single techniques to complete attack campaigns mapped to real threat actors.
Attack Actions: Atomic Cloud-Native Security Tests
Think of attack actions as the fundamental units of adversary behavior, atomic security tests that emulate one or more techniques threat actors actually use to compromise cloud infrastructure. Unlike traditional penetration testing tools that were retrofitted for cloud environments, Mitigant CAE attack actions are cloud-native by design. They understand cloud APIs, respect cloud architecture, and operate within the cloud's security model rather than fighting against it.
Each Mitigant CAE attack action targets specific cloud services and maps directly to MITRE ATT&CK techniques. More importantly, they're tagged with the threat actors known to use them, informed by validated CTI rather than theoretical frameworks. For example, the "Windows VM Custom Script Extension" attack action emulates a post-exploitation technique where attackers abuse Azure's legitimate management features to install malicious software on virtual machines. This isn't a theoretical concern; APT29 and other sophisticated threat actors actively employ this technique.
Attack Scenarios: Composing Multi-Step Reality
Real-world attacks don't occur in isolation. Adversaries don't simply execute a single technique and declare victory. They chain techniques together in carefully orchestrated sequences designed to achieve specific objectives. A ransomware attack might start with reconnaissance, progress through privilege escalation, establish persistence, exfiltrate data for double extortion, and finally encrypt systems. Each phase employs different techniques, targets different cloud services, and triggers different defensive mechanisms.
This is where attack scenarios become essential. Mitigant CAE attack scenarios build on attack actions like LEGO bricks by combining two or more atomic actions in specific sequences to emulate realistic, multi-step attack campaigns. The modular design means security teams can compose custom scenarios that match their specific threat model or leverage pre-built scenarios based on documented threat actor campaigns in CTI reports.
Mitigant CAE offers two types of attack scenarios that serve different but complementary purposes: managed attack scenarios and custom attack scenarios.
Managed Attack Scenarios
Attack scenarios emulate specific attack campaigns described in authoritative CTI reports. These are curated, maintained, and updated by Mitigant as new threat intelligence emerges. When a new APT group surfaces with novel techniques, when ransomware gangs pivot to new tactics, when cloud-specific attack patterns appear in the wild, managed scenarios get updated to reflect this evolving reality. Security teams benefit from this continuous refresh without needing to become CTI experts themselves.
For example, a managed attack scenario might emulate the Scattered Spider threat actor's complete attack chain: initial access through valid credential theft, privilege escalation within Entra ID, lateral movement to high-value cloud resources, and ultimately data exfiltration for extortion. Each step maps to documented Scattered Spider TTPs, which have been observed in the wild.
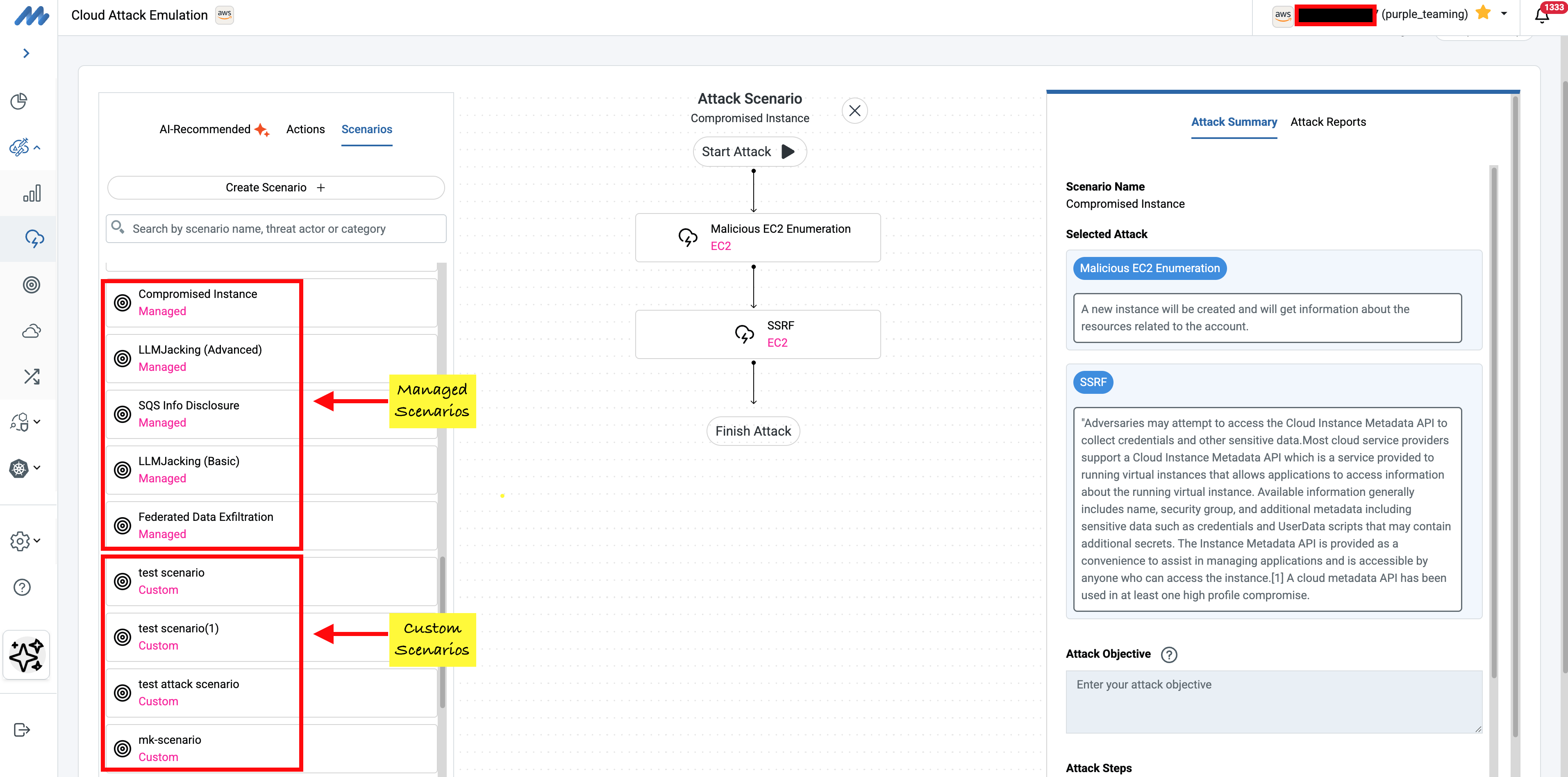
Custom Attack Scenarios
Custom attack scenarios empower security teams to build scenarios tailored to their unique environments, threat models etc. This is designed to enable flexibility for building attacks suited for contextual use cases e.g. to align with specific high-value assets warranting focused testing or recent CTI specific to an industry vertical.
Building custom scenarios is straightforward: select the relevant attack actions from the library, arrange them in the desired sequence and execute. The platform handles orchestration, manages dependencies between steps, collects comprehensive telemetry at each phase, and ensures proper cleanup afterward. This democratizes red teaming capabilities that were previously available only to organizations with dedicated offensive security teams or those who could afford hiring external consultants.
The multi-step nature of scenarios reveals something that individual attack actions cannot: the effectiveness of your defense-in-depth strategy. For example, security groups might fail to block initial intrusion attempts, and an EDR might miss privilege escalation steps, but catch the persistence mechanism. Also, attack scenarios help configuration of SIEMs to correlate events across the attack chains and alert during lateral movement.
Attack Orchestration Strategies
Mitigant CAE employs an intuitive and effective approach to attack orchestration that fosters balance between safety and realism. The attack orchestration consists of two execution strategies: inline attacks and provisioned attacks. These executions strategies are applied for both attack actions and attack scenarios, lets discuss these strategies briefly.
Inline Attacks
These attacks target existing cloud resources in your environment. These attacks operate against actual S3 buckets, running EC2 instances, deployed Lambda functions, and Bedrock resources. The value here is unmatched realism; you're testing your actual security posture, not a sanitized lab environment. If your CSPM tool reports an S3 bucket misconfiguration, an inline attack proves whether that misconfiguration is actually exploitable or merely theoretical noise. Inline attacks require sophisticated orchestration to safely execute against cloud environments (pre-production and production resources). Mitigant CAE automatically handles several sophisticated operations sutiable for safe and successful attacks including resource discovery, permission checks, state capture, dependency resolution, safety guardrails and rollback.
Provisioned Attacks
Provisioned attacks function by spinning up temporary infrastructure to safely emulate attack techniques without risking production systems. This approach is designed for attacks that could potentially cause service disruption or data loss; Mitigant CAE automatically creates isolated resources, executes attacks, collects telemetry, and cleans up the attacked resources afterward. This approach provides the safety teams need to test realistically without fear of taking down critical systems.

The intelligence lies in the automatic selection. CAE analyzes your cloud environment's context and determines which strategy makes sense for each attack action. A reconnaissance attack that merely lists S3 buckets? That runs inline safely. A data exfiltration simulation? That might require resource creation to avoid touching sensitive production data. Security teams don't need to make these decisions manually; the platform handles the complexity.
This stands in stark contrast to traditional Breach and Attack Simulation tools and to several open-source tools that typically spin up entirely disposable shadow environments. While those approaches guarantee safety, they sacrifice the very thing that matters most: testing whether your actual security controls, configured in your specific way, actually work. Attackers don't politely target your test environment; they target production. Your validation strategy should do the same, with appropriate safety guardrails in place.
Threat-Informed Defense in Practice
Threat-Informed Defense allows organizations shift from chasing vulnerability metrics to focusing on the threats that really matter by combining CTI, implemented security measures and adversary emulation. This approach is effective as it helps to prioritize threats and validate that the implemented measures effectively prevent attacks. Check out this blog post where we practically demonstrated how to implement Threat-Informed Defense together with our partner; sekoia. While most organizations look at Threat-Informed Defense and Gartner's CTEM as two separate strategies, we see these two as complimentary and actually a powerful synergy.
The Intelligence-Driven Validation Gap
The cybersecurity industry has embraced the concept of Threat-Informed Defense; the idea that defensive strategies should be shaped by actual adversary behavior rather than checkbox compliance or vendor feature lists. Organizations invest heavily in CTI feeds and hire analysts to understand what threat actors are doing. Yet a critical gap persists: how do you know if your defenses actually work against the threats you're monitoring?
This is the validation gap that Mitigant CAE fills by integrating CTI directly into the attack emulation process, thereby creating a continuous feedback loop between implemented security measures (e.g., security tools deployed), CTI, and validation efforts. When CTI reports indicate that APT29 is actively targeting cloud environments with specific techniques, CAE doesn't just document this information; it lets you test whether your security tools would prevent, detect, or recover from these techniques.

Most attack actions and scenarios in Mitigant CAE carry threat context: which threat actors use this technique, which campaigns have employed it, what the typical objectives are, and which industries are most frequently targeted. This context transforms abstract attack emulation into targeted, relevant validation. Instead of testing against a generic "bad actor," you're validating your defenses against the specific adversaries most likely to target your organization.
Consider a financial services organization monitoring intelligence about the threat actor Scattered Spider, rather than hoping their security controls would work, they can execute attacks specifically tagged with "Scattered Spider techniques" against their cloud infrastructure. The results provide empirical evidence: these techniques were blocked by our controls, those techniques bypassed our defenses, and here's the telemetry proving it.
Leveraging MITRE ATT&CK Correctly
MITRE ATT&CK remains invaluable for understanding adversary tactics, techniques, and procedures. The framework provides a common language for discussing threats, a structured way to document defensive coverage, and a foundation for threat-informed strategies. The problem isn't ATT&CK itself; it's the misuse of coverage percentages as a proxy for security effectiveness.
Mitigant CAE uses ATT&CK as intended: as a framework for understanding adversary behavior, not as a checklist for vendors to claim coverage percentages. Every attack action maps to specific ATT&CK techniques with precision. But rather than stopping at mapping, CAE goes further: it proves whether your detections for those techniques actually work.
This is the crucial distinction. A vendor claiming "T1078 Valid Accounts coverage" might mean they have a detection rule that could theoretically trigger if someone uses stolen credentials. CAE validates whether your specific detection implementation actually detects this technique when executed in your cloud environment with your specific configuration, using different procedures of the technique. The difference between theoretical coverage and empirical validation is the difference between hoping you're secure and knowing you're secure.
Implementing CTEM with Mitigant CAE
The Continuous Threat Exposure Management (CTEM) framework has gained traction as organizations recognize that point-in-time security assessments no longer keep pace with the rapidly evolving threat landscape. CTEM advocates for a continuous cycle: discover assets, prioritize based on risk, validate exposure, mobilize remediation, and repeat. This cycle acknowledges that security posture is dynamic, not static; new vulnerabilities emerge, exposures change, and attackers evolve.
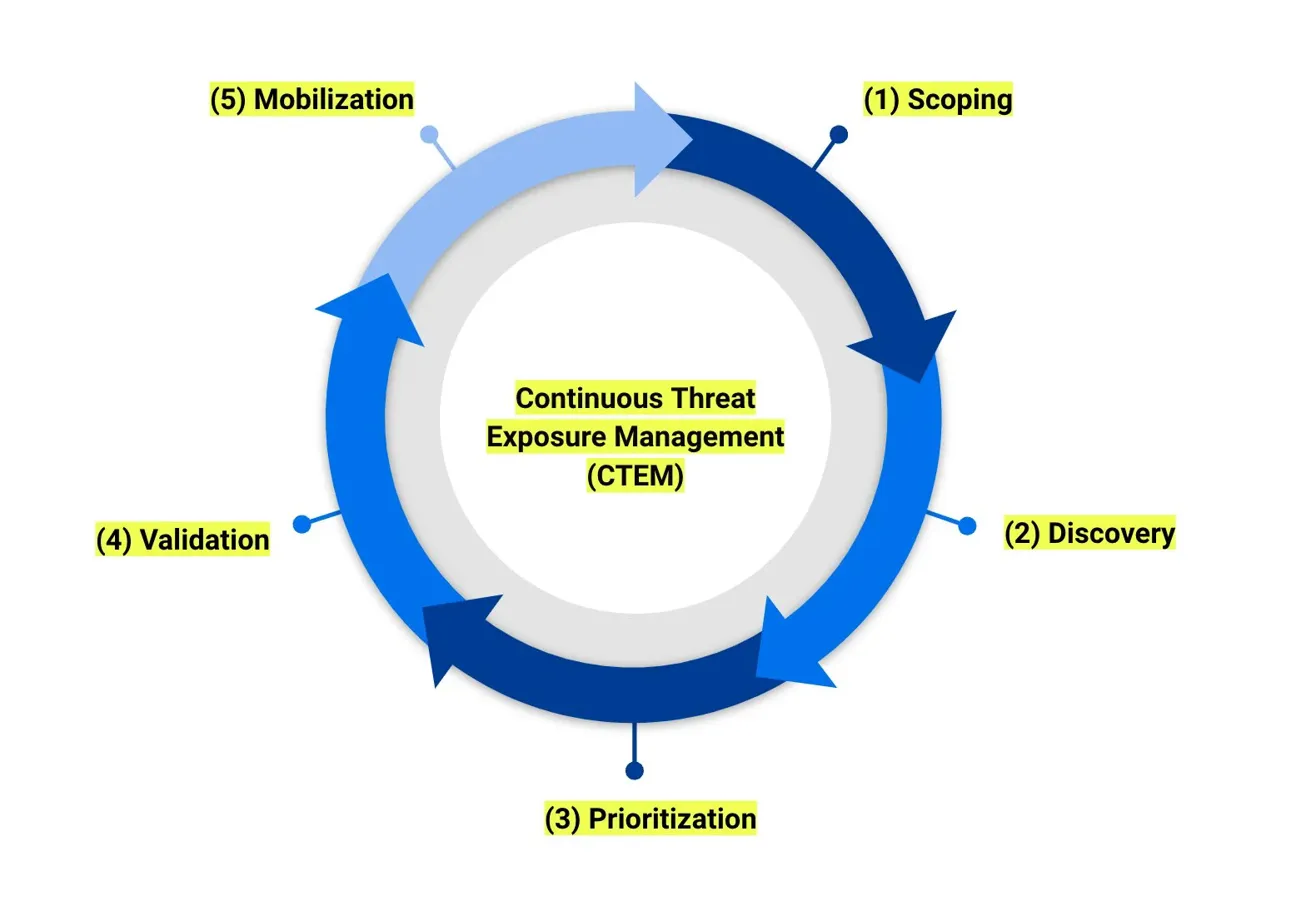
Mitigant CAE naturally fits into the CTEM prioritization and validation steps, providing the empirical evidence needed to move from theoretical exposure to proven exploitability. Cloud security tools like CSPM and CNAPP identify thousands of misconfigurations. But which ones actually matter? Which vulnerabilities can attackers realistically chain together to achieve impact? Which misconfigurations are exploitable versus merely non-compliant?
CAE answers these questions by providing a prioritized list of findings and by attempting actual exploitation in a controlled manner. The results inform prioritization: vulnerabilities that CAE successfully exploits jump to the top of the remediation queue, while theoretical issues that couldn't be weaponized get deprioritized. This data-driven approach to vulnerability management dramatically improves efficiency. Security teams stop chasing down every CSPM alert and focus on remediating actual exposure.
The continuous aspect is crucial in cloud environments, where change is constant. Infrastructure-as-code deployments happen multiple times daily. Auto-scaling groups spin up new instances with potentially different configurations. Development teams launch new services that may not inherit proper security controls. CTEM with CAE quickly catches these drifts, and scheduled attack scenarios continuously validate that new deployments maintain the expected security posture.
Organizations implementing CTEM with integrated attack emulation report a fundamental shift in how security teams operate. Instead of being reactive, responding to alerts about possible vulnerabilities, they become proactive, continuously validating that defensive investments actually reduce exploitable exposure. This shift from hope-based security to evidence-based security transforms organizational risk management.
Attack ReRun Mechanisms: Validating Security Improvements
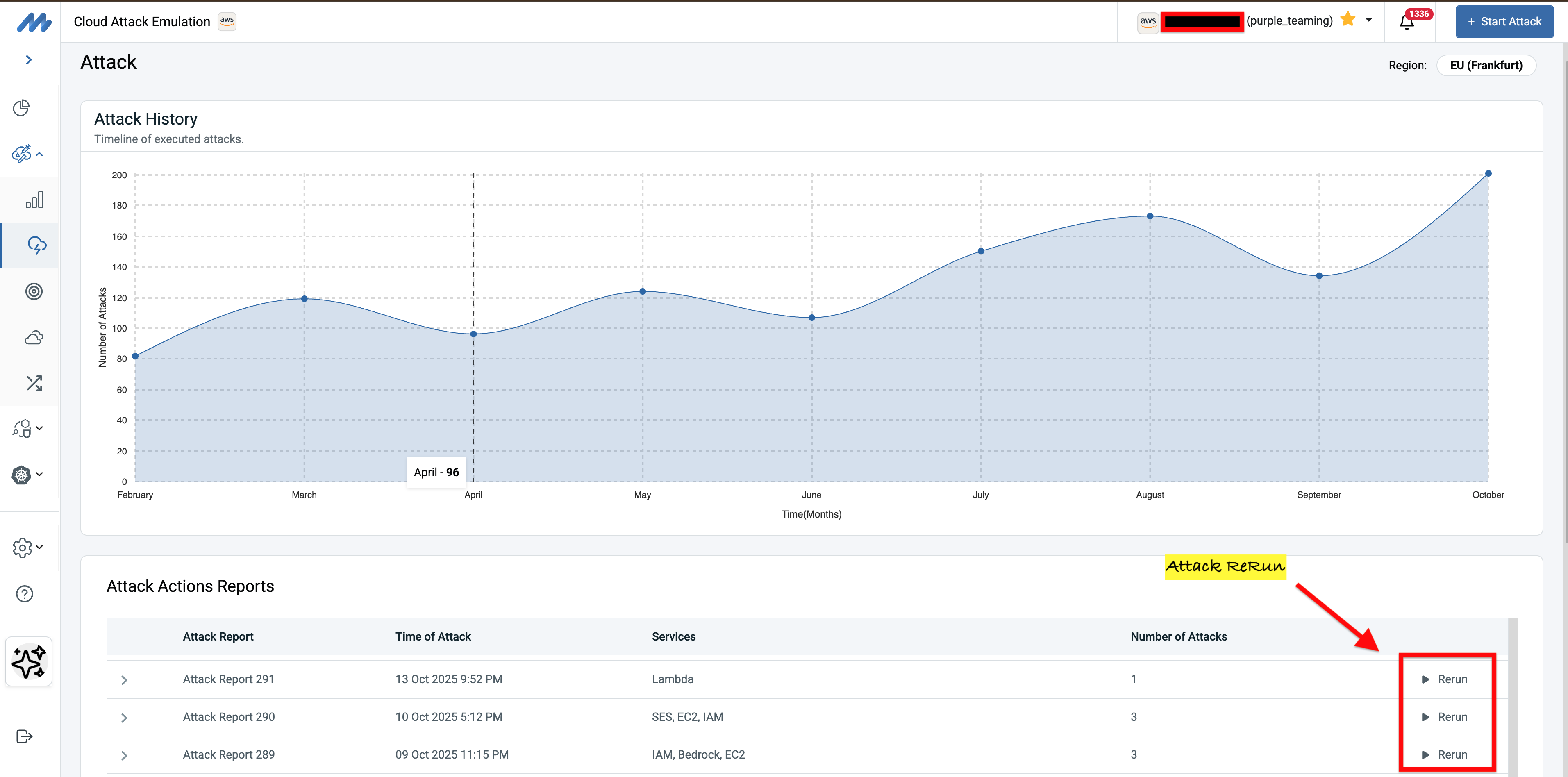
One of the most valuable aspects of continuous security validation is the ability to prove that remediation efforts actually work. When an attack successfully exploits a vulnerability or misconfiguration, security teams need a straightforward way to verify that their fixes are effective without manually recreating the entire test scenario.
Mitigant CAE's attack-rerun capability elegantly addresses this need. Every attack execution is automatically tagged and its results preserved, including detailed information about which specific resources were successfully compromised. After security teams implement hardening measures, they can simply retry the exact same attack against the exact same resources with a single click.
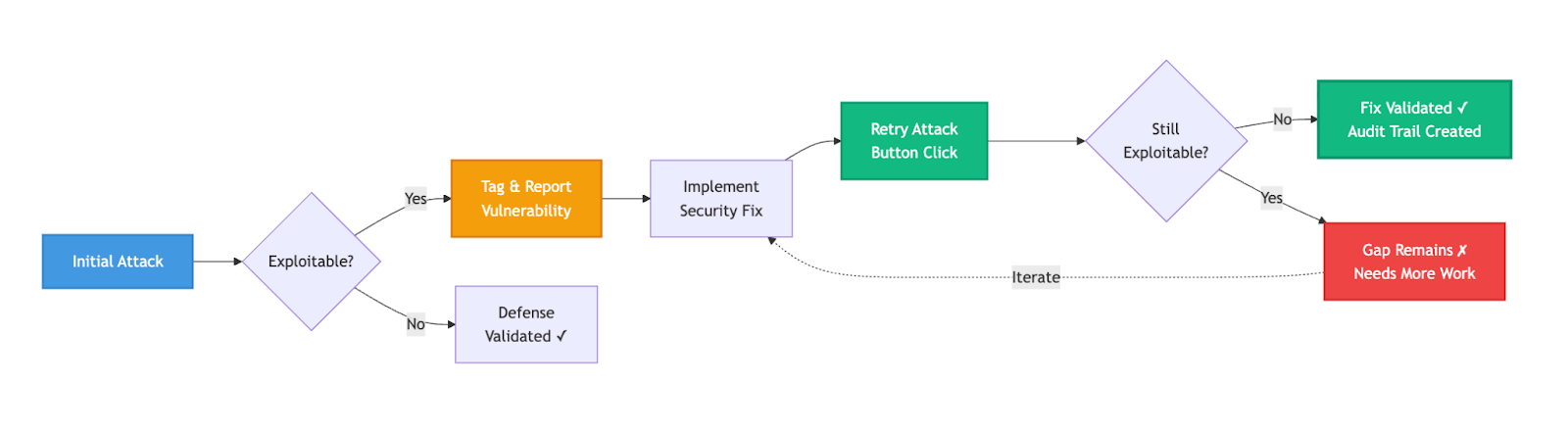
This targeted re-testing approach transforms remediation validation from a labor-intensive process into an efficient workflow. Consider a scenario where an attack successfully exfiltrated data from a specific S3 bucket due to overly permissive access policies. The security team updates the bucket policy and applies the Principle of Least Privilege. Rather than manually reconstructing the attack scenario, configuring target parameters, and hoping they're testing the right thing, they simply select "Retry Attack" from the historical report. CAE automatically re-executes the identical attack sequence against that specific S3 bucket, providing immediate empirical evidence of whether the remediation was successful.
The retry mechanism maintains a complete attack context: the original resource identifiers, the attack action sequence, the specific techniques employed, and the original results for comparison. This creates an audit trail that shows improvements in security posture over time. Teams can demonstrate to stakeholders that vulnerabilities identified in previous assessments have been genuinely remediated, not just marked as "closed" in a ticketing system without validation.
This smooth validation approach aligns perfectly with the CTEM methodology discussed earlier. The validation stage doesn't end when attacks are executed; it continues through remediation and re-validation, ensuring that security improvements actually reduce exploitable exposure rather than just creating the appearance of progress. Security teams shift from hoping their fixes work to knowing their fixes work, backed by empirical evidence from repeated attack emulation.
Attack Methodology: Design for Safety
Effective offensive security testing requires balancing realism against production risk, and Mitigant's hybrid methodology achieves both through intelligent automatic selection of attack strategies combined with deterministic recovery mechanisms.
The Hybrid Approach to Realistic Testing
The central tension in offensive security testing has always been the tradeoff between realism and safety. Test too aggressively against production systems, and you risk outages that cost the business. Test too conservatively in isolated lab environments, and you validate nothing meaningful about your actual security posture. Most organizations resolve this tension by leaning toward safety, which explains the proliferation of penetration testing against dedicated test environments that bear little resemblance to production.
Mitigant's hybrid approach dissolves this false dichotomy. By intelligently combining inline attacks and provisioned attacks, CAE achieves both realism and safety without compromise. For example, consider testing data exfiltration defenses. An inline approach would attempt to exfiltrate actual sensitive data from your production S3 buckets unacceptably risky for obvious reasons. Instead, CAE automatically creates a temporary S3 bucket, populates it with mock sensitive data, applies similar access controls to your production buckets, and attempts to exfiltrate data from this controlled resource. Your Data Loss Prevention systems, CloudTrail monitoring, and SIEM correlations all function identically whether the bucket is production or test, so the detection validation remains authentic while eliminating data breach risk.
Conversely, testing whether your monitoring detects reconnaissance activities, such as enumerating IAM roles or listing S3 buckets, poses minimal risk when executed inline against production. These read-only operations don't modify state or access sensitive data, yet they provide the most realistic validation of whether your Cloud Detection and Response tools actually alert on suspicious enumeration patterns. CAE executes these inline to maximize detection realism.
This intelligent selection happens automatically based on attack taxonomies and risk scoring. Security teams don't need to become experts in cloud architecture or attack safety to use CAE effectively. The platform handles complexity behind a simple interface: select the attacks relevant to your threat model, execute them, and review the results.
Automatic Recoverability: The Dynamic Snapshot Advantage
One of the most significant barriers to organizations running realistic security testing is the fear of irreparable damage. What if production workloads are impacted during the attack? What if the cleanup process fails? What if cloud resources end up in an inconsistent state that causes production issues? These concerns are legitimate and have been equally expressed against traditional penetration testing and purple teaming exercises.
Mitigant CAE addresses these concerns through the dynamic snapshotting strategy; an approach resulting from the innovative academic research by Mitigant founders. This strategy leverages a unique recovery mechanism that guarantees resources return to their pre-attack state. Before any attack executes, CAE automatically captures detailed snapshots of target resources for post-attack recovery.
After the attack execution completes, whether successful or not, the recovery process automatically runs. Modified resources are restored to their pre-attack state; created resources are deleted, and access policies are reverted. The environment returns to its original state before testing began. This deterministic rollback provides the confidence needed to test realistically without fear of lingering impact.
Importantly, the recovery mechanism operates independently of the attack itself. Even if an attack action fails mid-execution due to unexpected errors, the recovery process still runs based on previously captured snapshots. This separation of concerns ensures that cleanup reliability isn't dependent on attack code behaving perfectly; a critical design decision for production-oriented testing.
The dynamic nature of this snapshotting distinguishes it from static backup strategies. CAE doesn't require you to manually create test environments, back them up, and restore them between tests. The entire snapshot-attack-recover cycle happens automatically, enabling the kind of frequent, continuous validation that CTEM demands.
Moving from Shallow to Deep: The Journey Continues
We've now waded through the shallow waters of Cloud Attack Emulation, understanding the fundamental building blocks: attack actions as atomic tests, attack scenarios as realistic multi-step attacks, threat-informed defense that moves from coverage claims to empirical validation, and safety mechanisms that enable realistic testing without risk. These foundations enable the shift from theoretical security postures to evidence-based defense.
Sneak Peak Into Part III
But understanding how attacks work is only the beginning. The real value emerges when you examine what attacks reveal: detection gaps that need remediation, evidence-based validation of defensive investments, and actionable intelligence about your security effectiveness. Part III of this series dives into these deeper waters, exploring attack detection validation, Gen AI red teaming for modern workloads, automation through scheduling and APIs, and ultimately answering the question: how is Cloud Attack Emulation fundamentally different from traditional Breach & Attack Simulation and penetration testing?
Get Started with Mitigant CAE
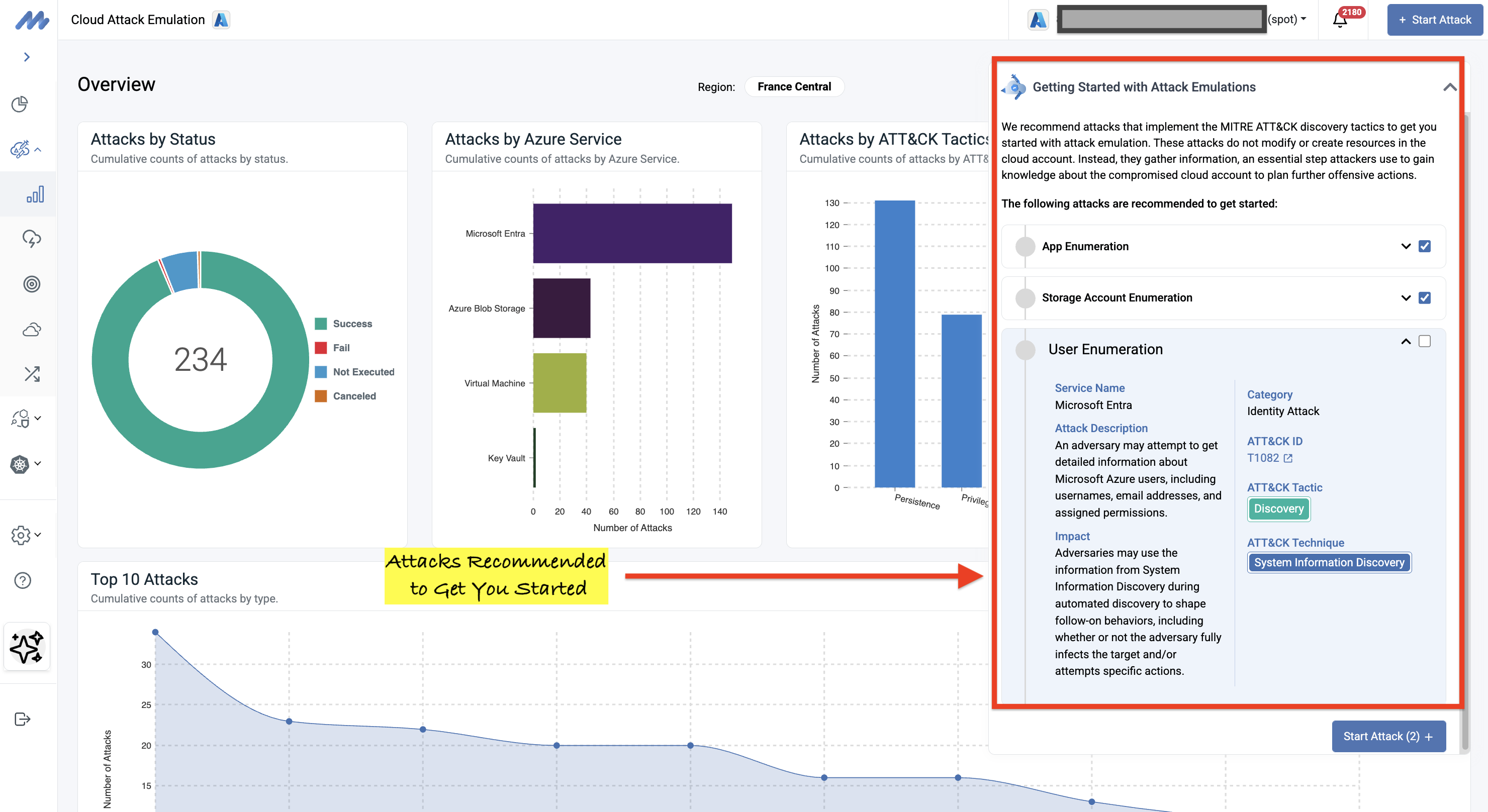
For now, consider taking your first steps into these shallow waters. Start with enumeration and discovery attack techniques under the MITRE ATT&CK Discovery tactic that are completely harmless, create no resources, and modify nothing. These noisy but benign attacks let you safely validate whether your detection systems actually alert on reconnaissance activities that precede more dangerous attack phases. They're the perfect entry point for teams building confidence in adversary emulation.
As security teams shift from coverage claims to detection reality, from compliance-driven security to threat-informed validation, from point-in-time assessments to continuous exposure management, Cloud Attack Emulation provides the empirical foundation that modern cloud security demands. The attack primitives, threat-informed scenarios, and safety mechanisms covered in this article form the technical substrate enabling that transformation.
Sign up for your Mitigant CAE free trial and begin validating whether your cloud security controls actually work, not according to vendor coverage percentages, but according to empirical evidence from your specific environment: https://www.mitigant.io/en/sign-up
Alternatively, if you just want to experience the power of Cloud Attack Emulation without onboarding your cloud environment, get access to our demo environment here - https://www.mitigant.io/en/sign-up-demo





.png)

