Feature Release: Leveraging AI for Adversary Emulation


Over the past year, we've observed a consistent pattern across organizations. Security teams run cloud attack emulations and generate detailed reports, but they struggle with three critical issues:
- Analysis Paralysis: While comprehensive attack reports are provided, some teams still struggle to get a quick overview, especially of the attack emulation, affected resources, impact/implications, and necessary countermeasures.
- Context Gap: Our attack library currently has over 200 attacks cutting across AWS and Azure cloud services. Knowing which of these attacks would be most beneficial to a cloud environment often requires some research and a deep understanding of the cloud environment and threat landscape. This is typically part of the red/purple teaming process; however, we aim to reduce the time spent on research and also lower the barrier for non-specialists.
- Blast Radius Control: Organizations adopting cloud attack emulation want greater control over the blast radius of emulated attacks. Though Mitigant CAE has several in-built safety measures, we want to further enhance these capabilities by empowering our customers with even finer control by tightening the permissions used for attack emulations.
Consequently, we are excited to announce three groundbreaking features that address these concerns and ultimately represent a significant leap forward in cloud attack emulation and offensive security testing: AI-Powered Attack Report Summarization, AI-Powered Attack Recommendations, and Bring Your Own Role (BYOR). These capabilities address real pain points we've heard from security practitioners and reflect our commitment to making offensive security testing more accessible, contextual, and under your control.
Details of these new features are discussed in the following sections.
AI Attack Report Summarization: Cut Through the Noise
Our new AI-powered summarization transforms dense attack reports into clear, actionable intelligence. Instead of wading through pages of technical details, security teams now get an executive summary that immediately answers critical questions, including:
- What happened: A concise description of the attacks executed.
- What was targeted: The specific services and resources involved
- What's the impact: The severity of the impact of the emulated attack, i.e., if it occurred in reality.
- What should we do: Prioritized remediation recommendations.
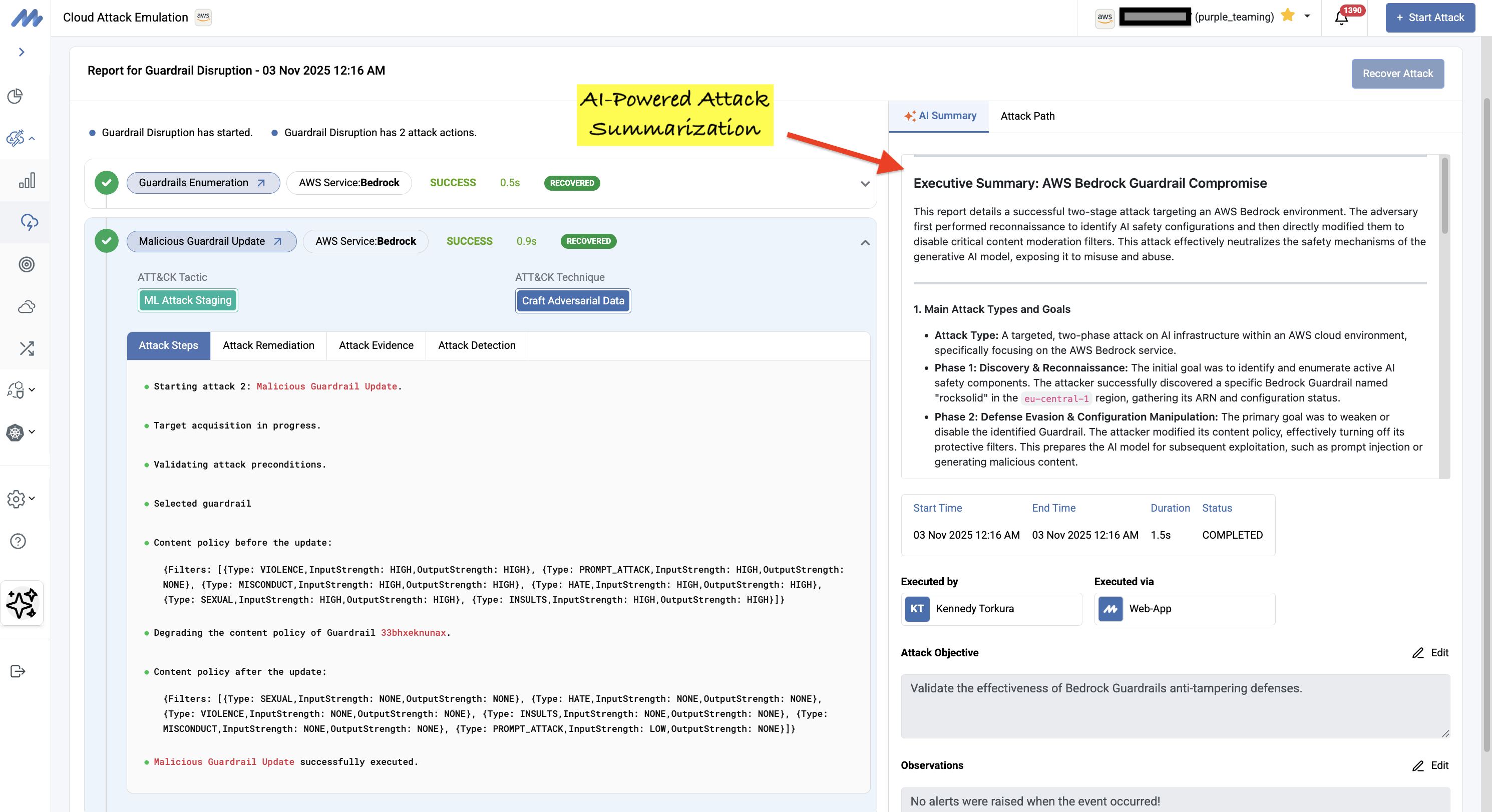
Here's a real example from a recent Bedrock Guardrail Disruption attack. The AI summary immediately distilled the complex two-phase attack into clear, actionable intelligence. This wasn't just reconnaissance; it was a successful compromise of AI safety mechanisms:
Phase 1: Discovery &Reconnaissance - The attacker enumerated a Bedrock Guardrail named "rocksolid" in the eu-central-1 region.
Phase 2: Defense Evasion- The attacker modified the guardrail's content policy, disabling protective filters for HATE, VIOLENCE, SEXUAL, INSULTS, and MISCONDUCT
The AI summary provided:
• Attack Classification: Two-phase attack on AI infrastructure (Discovery + Defense Evasion)
• MITRE ATT&CK and MITRE ATLAS mappings: Cloud Infrastructure Discovery (T1580), Discover ML Artifacts (ML0001), Disable Cloud Firewall (T1562.011)
• Impact Assessment: Critical risk; complete compromise of AI model's safety integrity, exposing the model to prompt injection, jailbreaking, and content misuse
• Prioritized recommendations: Implement least privilege for bedrock:UpdateGuardrail permissions, enable CloudWatch alarms for UpdateGuardrail API calls, enforce change management for AI safety configurations, and implement drift detection.
This level of clarity, transforming raw API calls and technical logs into a narrative that security leaders can immediately understand and act on, happens automatically for every attack emulation, dramatically reducing the time from testing to remediation.
AI-Powered Attack Recommendations: Context is King
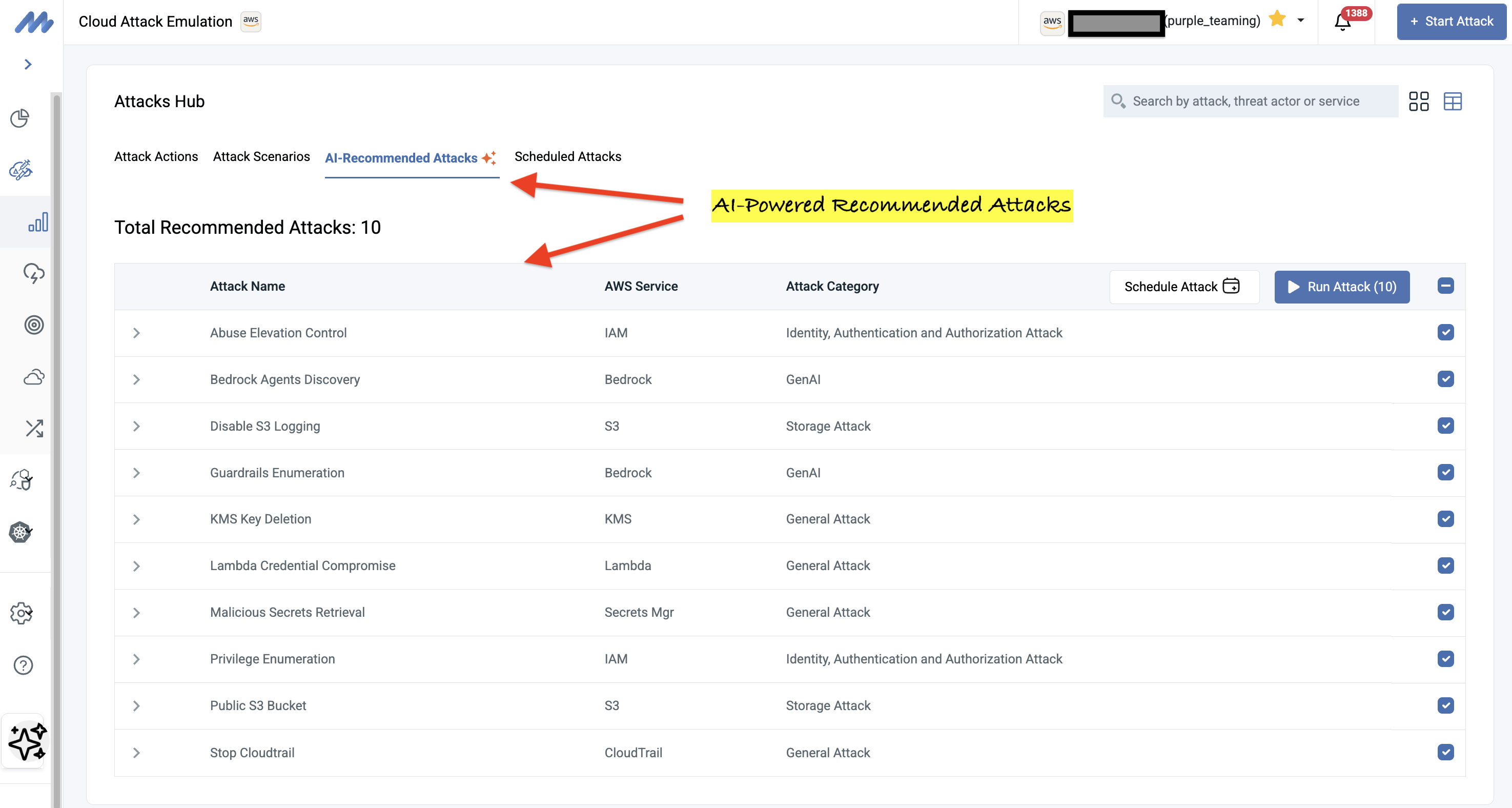
Not all attacks are relevant to cloud environments; for example, running Lambda attacks in environments where Lambda functions are not used is not optimal. The newly released AI-Powered Attack Recommendations feature solves this by intelligently analyzing your actual cloud environment and suggesting attacks that matter to your specific setup.
Here's how it works: The feature begins by leveraging Mitigant CSPM to perform a comprehensive analysis of your cloud environment. This deep assessment identifies existing weaknesses, misconfigurations, and security gaps across your infrastructure. Armed with this contextual knowledge, our AI then recommends specific attacks that would have the greatest impact on your environment.
This approach fundamentally changes how organizations prioritize security testing. Instead of running hundreds of attack emulations hoping to find issues, you're guided toward high-severity, high-impact scenarios that matter most to your specific security posture. The system understands:
- Which AWS services are you actually using, and how are they configured?
- The current security posture identifies weaknesses from CSPM analysis.
- Attack paths that are realistic and exploitable, given your architecture
- The potential business impact of successful attacks against your specific setup
- MITRE ATT&CK tactics most relevant to your environment
For example, if the CSPM discovers overly permissive IAM policies combined with Amazon Bedrock deployments, the AI will prioritize recommending "Guardrails Enumeration" and "Privilege Escalation via IAM" attacks, as these pose the greatest risk to your specific environment, not just theoretical scenarios.
But the value doesn't stop at recommendations. By running these AI-suggested attacks, organizations can:
- Validate discovered gaps: Confirm that the weaknesses identified by CSPM are actually exploitable
- Leverage remediation guidance: Receive specific, actionable steps to close the validated security gaps
- Implement Sigma detection logic: Deploy the recommended Sigma rules to detect and alert on these attack patterns going forward. There might be a need to convert the provided Sigma logic to the specific format used by your threat detection system.
This creates a powerful feedback loop: discover vulnerabilities through CSPM, validate them through targeted attack emulation, remediate with confidence, and establish detection capabilities to prevent future exploitation.
The contextual approach delivers measurable benefits:
- Efficiency: Focus testing efforts on real, exploitable weaknesses where they matter most.
- Prioritization: Test high-severity, high-impact scenarios first instead of wasting time on low-risk attacks
- Realism: Emulate attacks that real adversaries would attempt against your specific infrastructure.
- Validation: Prove that the identified weaknesses are actually exploitable before investing in remediation.
- Defense-in-depth: Build detection capabilities alongside remediation efforts.
Each recommendation includes the attack name, target AWS service, potential impact assessment, and corresponding ATT&CK tactics (Privilege Escalation, Discovery, Defense Evasion, Credential Access, Impact), giving you a comprehensive view of how different attacks fit into broader adversary campaigns tailored to your environment.
Bring Your Own Role: Security Through Controlled Access
This feature represents a philosophical shift in how we think about cloud attack emulation platforms. We recognize that giving any external platform offensive capabilities in your cloud environment requires an extraordinary level of trust, and that trust must be earned through transparency and control.
Bring Your Own Role (BYOR) allows organizations to onboard to Mitigant CAE using their own custom IAM role instead of our default configurations. This is particularly important for security-conscious organizations that want to:
- Define exact permissions granted to the Mitigant platform.
- Implement custom trust relationships with additional security layers.
- Meet compliance requirements that mandate specific IAM configurations.
- Maintain audit trails in accordance with their own governance frameworks.
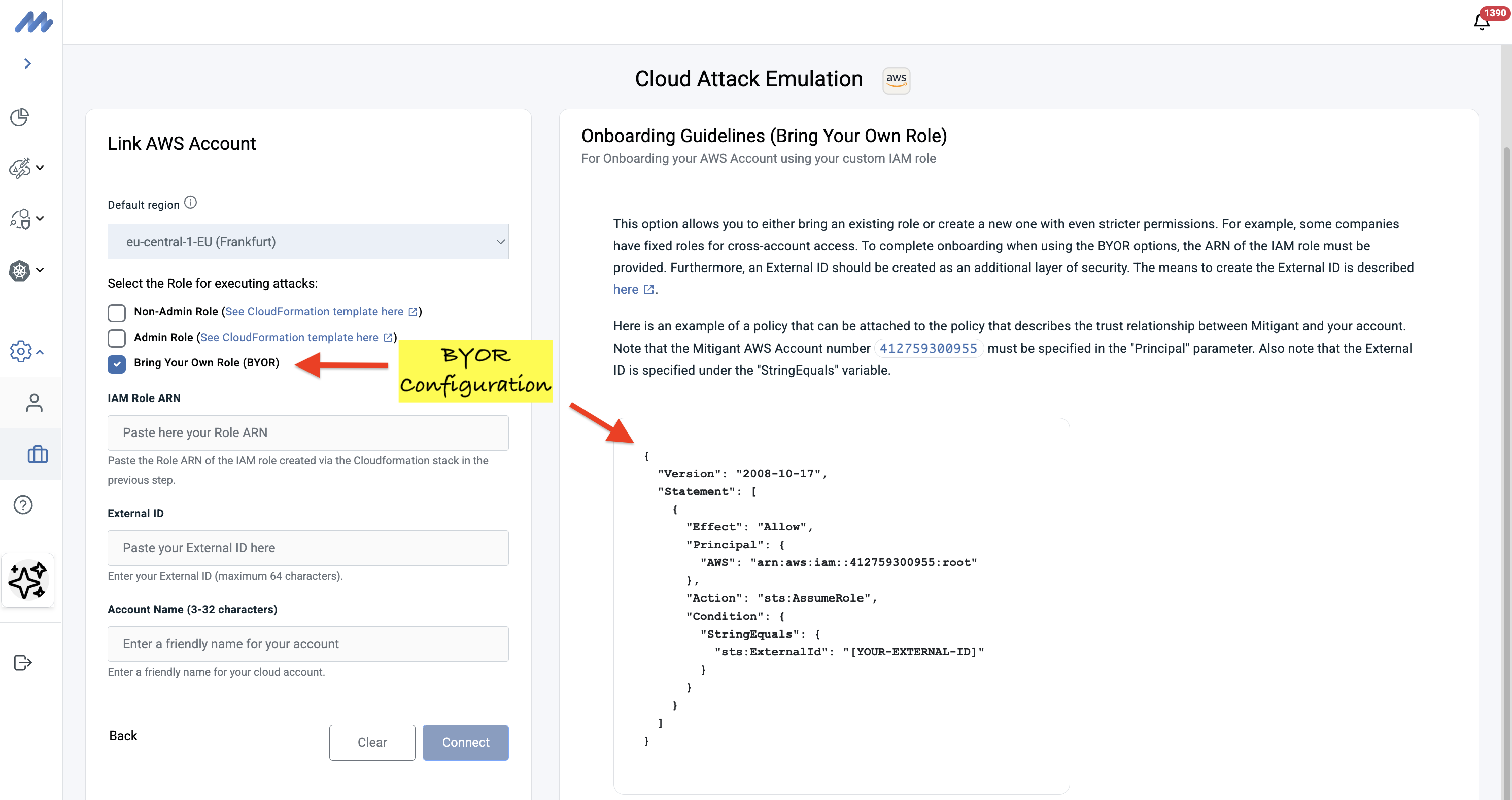
The BYOR workflow guides you through creating an IAM role with precisely the permissions you're comfortable granting. You can:
- Create an IAM role or use an existing one.
- Customize the role based on the permissions you’d want to assign to the Mitigant platform.
- Add an external ID verification for enhanced security.
- Ensure that the correct trust relationships are implemented.
This level of control aligns with our recent discussions on safety in offensive security testing. BYOR ensures that organizations never have to choose between effective security testing and maintaining strict governance over their cloud environments. For teams concerned about attack emulation capabilities, this feature provides peace of mind: you define the boundaries, control permissions, and audit or revoke access at any time through your own IAM policies.

Example Scenario: Fusing The New Features Together
To see how these three features create a complete security testing lifecycle, consider this real-world workflow:
Step 1 - Secure Onboarding (BYOR): An organization with strict blast radius control requirements onboards to Mitigant CAE using a custom IAM role. They start conservatively, granting only permissions for non-destructive discovery attacks.
Step 2 - Intelligent Recommendations: Mitigant CSPM continuously analyzes their cloud environment, identifying misconfigurations and security gaps. The AI correlates these findings with our attack library and recommends high-impact attacks specific to their environment—such as IAM privilege escalation or S3 bucket enumeration.
Step 3 - Execute Attacks: The security team selects and runs the AI-recommended attack scenarios to validate whether the identified gaps are actually exploitable.
Step 4 - Instant Intelligence: The AI Attack Summarization feature automatically generates an executive summary for each attack, mapping it to MITRE ATT&CK, assessing business impact, and providing prioritized remediation steps.
Step 5 - Harden Environment: The team implements the recommended fixes and deploys Sigma detection rules to prevent future exploitation.
Decision Point: After several successful testing cycles, the organization faces a choice:
- Continue with current permissions: Loop back to step 2 and keep testing within existing boundaries
- Expand testing coverage: Increase confidence has been built, so they expand BYOR permissions to enable more sophisticated attacks (returning to step 1 with broader privileges)
This maturity model allows organizations to start small, build trust, and gradually expand their offensive testing capabilities as they gain confidence in the platform and their security posture improves.
The Bigger Picture: AI as a Security Force Multiplier
These features share a common thread: they use AI not to replace security practitioners, but to amplify their capabilities.
- Summarization reduces cognitive load, letting teams focus on decision-making rather than data processing.
- Contextual recommendations eliminate wasted effort, directing attention to high-value tests.
- BYOR provides governance and control, ensuring AI-powered testing remains aligned with organizational policies
Together, they represent our vision for the next generation of cloud security testing: intelligent, contextual, and always under your control.
Don't Wait. Get Started Today!
All three features are now available in Mitigant CAE:
- AI Summaries are automatically generated for all attack emulations; just look for the "AI Summary" tab in your reports.
- AI Recommendations appear in the attack library and the Mitigant CSPM overview.
- Bring Your Own Role can be selected during the onboarding process when connecting new AWS accounts.
We're continuing to enhance these capabilities based on customer feedback. If you have suggestions or questions about these features, please reach out to our team.
Want to see these features in action? Sign up for a free trial at https://www.mitigant.io/en/book-demo , alternatively, get access to our live demo environment https://www.mitigant.io/en/sign-up-demo






.png)
