CSPM Scans Are Not Cloud Penetration Tests: Understanding the Critical Differences


There's a dangerous misconception that a Cloud Security Posture Management (CSPM) scan is equivalent to performing a cloud penetration test. Fire up your favorite CSPM tool, export the findings report, and voilà: you have a pentest report.
Not so fast.
While CSPM tools are valuable for identifying misconfigurations and compliance gaps, they fundamentally differ from actual cloud penetration testing. Understanding this distinction isn't just semantic, it's critical to maintaining a robust cloud security posture. This misconception hurts everyone: consultants delivering cloud assessments, internal teams trying to maintain security, and organizations thinking they're protected when they aren't.
This blog post explores three dimensions of confusion driving this misconception: the fundamental differences between CSPM and cloud penetration testing, security culture and inadequate tooling, and how traditional penetration testing approaches fail in cloud environments. We then demonstrate how Mitigant Cloud Attack Emulation (CAE) systematically addresses each dimension, providing the production-ready security validation organizations need.
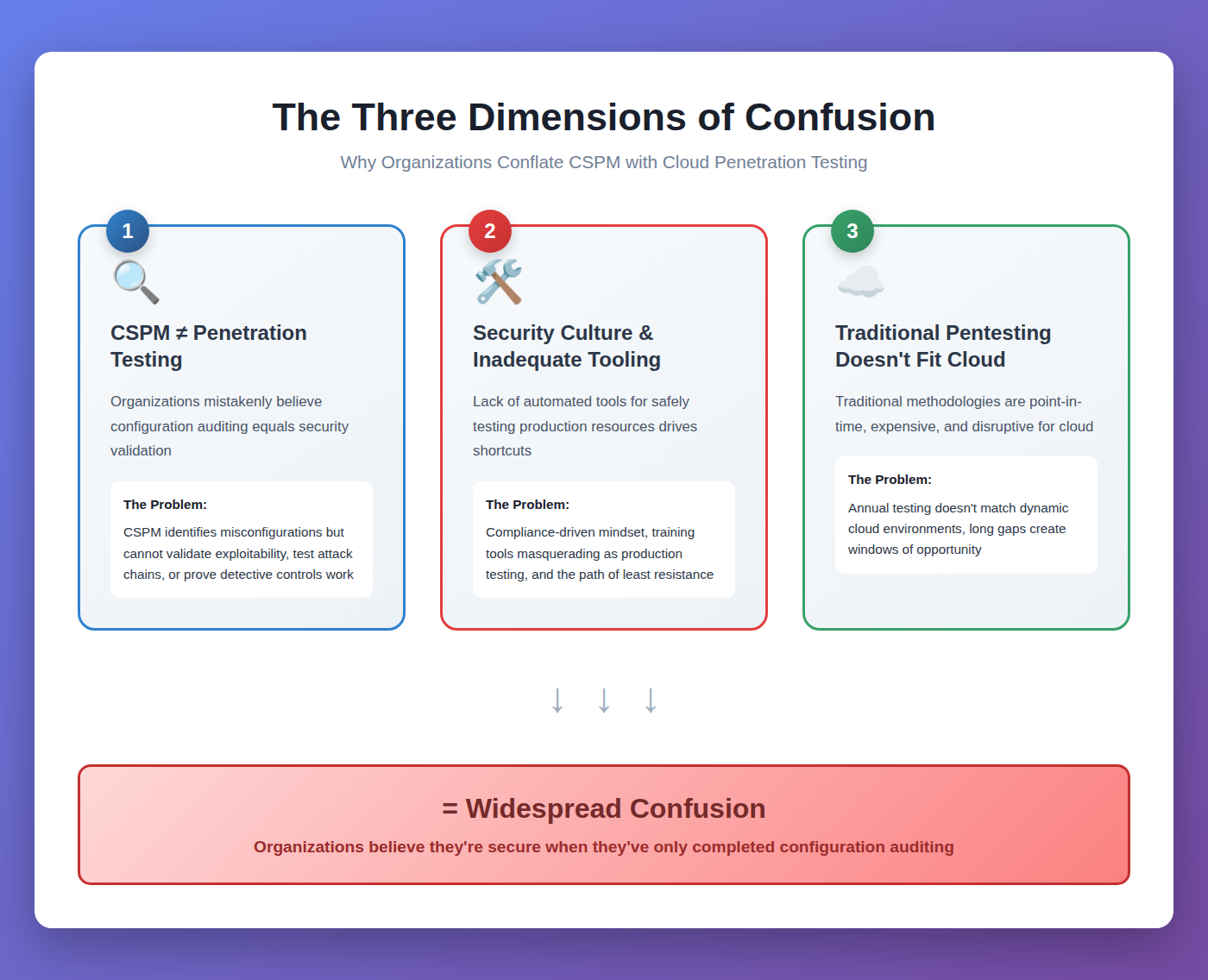
The Problem: Three Dimensions of Confusion
The confusion between CSPM and cloud penetration testing isn't simple: it exists across three distinct dimension, each contributing to the gap between perceived and actual security. Let's briefly discuss three confusion dimensions.
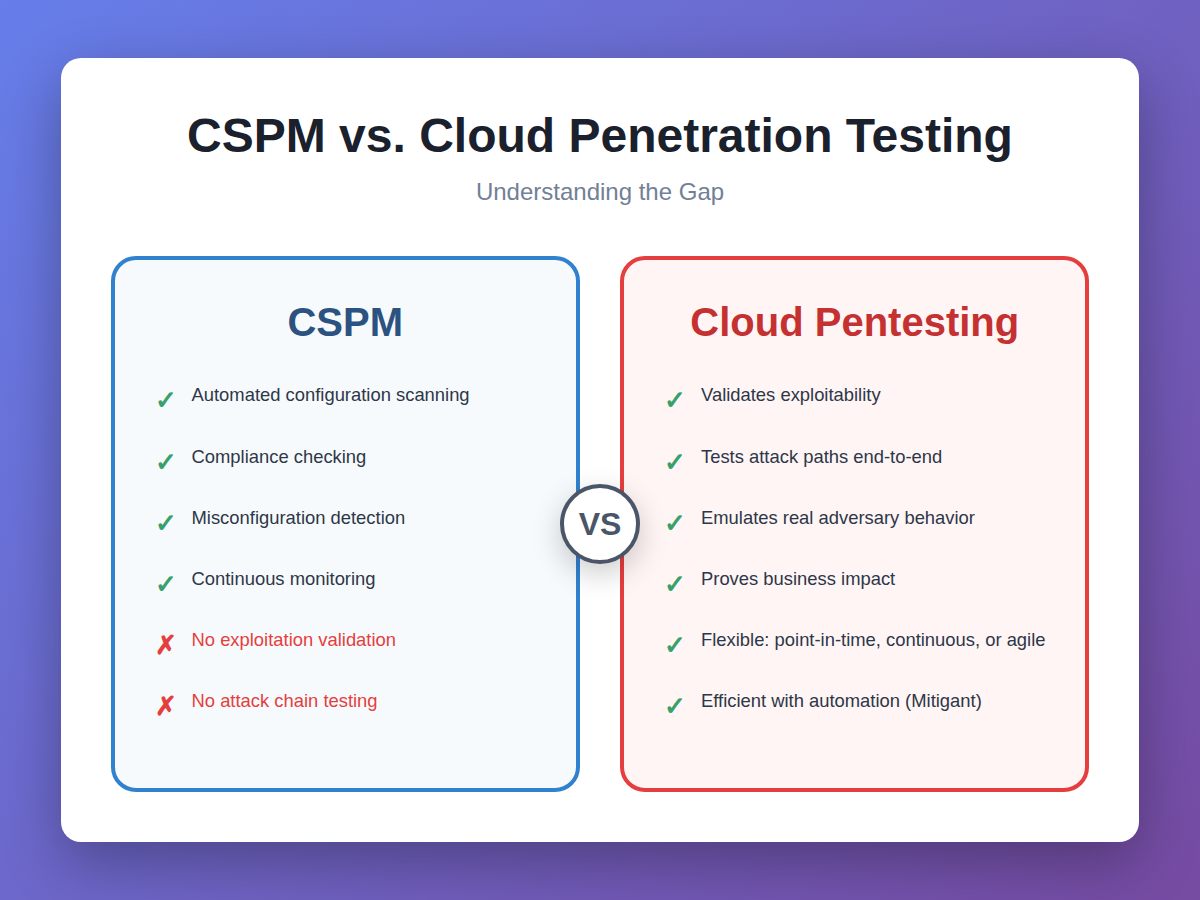
Dimension 1: CSPM ≠ Cloud Penetration Testing
What CSPM Actually Does
CSPM tools perform configuration auditing:a critical but fundamentally passive security activity. They inventory cloud resources across cloud environments, check configurations against security benchmarks like CIS and NIST, identify deviations from best practices, and detect publicly exposed resources and other forms of misconfigurations. They also map findings to compliance frameworks, generate compliance posture reports, track remediation over time, and provide audit trails. However, CSPM tools have four fundamental limitations:
1. Point-in-Time Assessments: CSPM captures the current state of cloud environment and identifies potential vulnerabilities, but it provides only a point-in-time snapshot. Cloud environments are highly dynamic, with infrastructure-as-code deployments happening multiple times daily, auto-scaling groups spinning up new instances, and development teams launching new services. By the time a CSPM scan completes and findings are reviewed, environments may have already changed significantly, making the assessment outdated and potentially missing new vulnerabilities introduced by recent changes.
2. Validation Gap: CSPMs can identify an S3 bucket configured for public access, but cannot verify whether it contains sensitive data, whether bucket policies actually prevent access, or whether logging would detect unauthorized access attempts. Furthermore, CSPMs can identify overly permissive IAM roles, but don't test whether an attacker could chain those permissions with other misconfigurations to escalate privileges, move laterally, or access critical resources.
3. Limitations of CSPM Attack Paths: Modern CSPMs have evolved to include graph-based attack path analysis that maps IAM permission chains, visualizes paths from internet-exposed resources to sensitive data, and calculates blast radius. While valuable for attack-surface mapping, these tools model theoretical attack paths without validating if attackers can exploit them. These reachability paths also stuggle to account for additional controls, such as VPC endpoint policies, runtime protections, or service-specific limitations, that may block exploitation attempts, leading to false positives: paths that appear exploitable on paper but fail when tested.
4. Security Control Validation: CSPM reports that CloudTrail logging is enabled, but doesn't verify whether SIEMs alert on suspicious API calls or if incident response procedures catch attacks. It tells you what's misconfigured but doesn't demonstrate the actual impact; the data that could be exfiltrated, the resources that could be compromised, or the blast radius of successful attacks.
What Real Cloud Penetration Testing Does
Actual cloud penetration testing goes far beyond configuration auditing. It's an adversarial assessment that emulates real attacker behavior against deployed cloud infrastructure.
Cloud penetration testing follows established methodologies adapted for cloud-native environments. The Cloud Security Alliance (CSA) Cloud Penetration Testing Playbook adapted traditional penetration testing principles to fit cloud-specific requirements using the STRIDE threat modeling framework (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege).
A comprehensive cloud penetration testing includes pre-engagement scoping, reconnaissance and enumeration, initial access attempts, privilege escalation, lateral movement, impact assessment, and crucially:detection validation. Unlike CSPM, penetration testing validates whether SIEM rules detect attacks, whether cloud-native detection services alert, and whether SOC teams can identify and respond to malicious/suspicious events. The process includes comprehensive reporting with MITRE ATT&CK mapping and evidence of exploitability, followed by iterative remediation testing to validate the effectiveness of fixes.
Dimension 2: Security Culture and Inadequate Cloud Security Tooling
A critical factor driving the confusion is the scarcity of automated tools for safely testing existing resources. This is an essential requirement in testing production environments.
The Blurring of Lines Between Configuration Auditing and Offensive Testing
This isn't the first time we've seen this pattern. A similar misconception exists in web application security: reports generated by automated vulnerability scanners are often conflated with penetration testing. Despite finding vulnerabilities, such scanners rarely validate exploitability, test chained attack techniques, or evaluate defensive controls. The same pattern has emerged in cloud security, where vendors market CSPM tools with language traditionally associated with offensive security testing, leading organizations to believe they've achieved comprehensive security validation when they've only completed configuration auditing.
Compliance-Driven Security: The Path of Least Resistance
Organizations facing audits and compliance requirements often seek the path of least resistance, making CSPM reports an attractive alternative to resource-intensive penetration testing. Most compliance frameworks such as SOC 2, ISO 27001, and PCI DSS require evidence of security testing, but they rarely specify the needed depth or methodology. A CSPM scan report satisfies auditor checkboxes at a fraction of the cost and effort of a comprehensive penetration test, creating a perverse incentive structure where organizations optimize for compliance rather than actual security. CSPM scans are non-disruptive, require no specialized expertise to interpret, can be scheduled automatically, and provide impressive-looking PDF reports with thousands of findings: all characteristics that make them appealing to compliance-focused organizations. However, this approach creates a dangerous disconnect: organizations achieve compliance certification while remaining vulnerable to real-world attacks that CSPM would never detect. The compliance checkbox gets marked, leadership believes security is validated, but the actual attack surface remains untested and potentially exploitable.
Why Production Testing Tools Don't Exist
Most existing cloud security testing approaches fall into two inadequate categories. Lab environment testing creates isolated test environments that bear little resemblance to production:security teams validate controls in sanitized conditions while attackers target actual production systems. The configurations, network topology, and security controls in test environments rarely mirror production environments accurately, so that successful tests can provide false confidence in the real-world security posture. Shadow infrastructure tools spin up disposable environments for testing, then tear them down afterward: excellent for training and learning, but useless for validating whether your actual security controls work as deployed.
Dimension 3: Traditional Penetration Testing Doesn't Fit Cloud
Traditional penetration testing methodologies do not fully apply to cloud infrastructure. The approaches have critical limitations: they are point-in-time, resource-intensive, expensive, and disruptive with long gaps between test and retest. The dynamic nature of cloud environments, the abstraction of cloud services, and the shared responsibility model all require specialized approaches that traditional methodologies weren't designed to handle.
Most traditional penetration testing tools were built for on-premises networks and later retrofitted for cloud, creating fundamental operational limitations. The core challenge is the tension between realism and safety: testing aggressively against production systems risks outages and data loss, while testing conservatively in isolated labs validates nothing meaningful about actual security. Most organizations resolve this by prioritizing safety over realism, which manifests as highly scoped engagements testing only narrow subsets of infrastructure, focusing on superficial external attack surfaces, or avoiding the internal cloud environment entirely ultimately yielding little actionable insight into actual exploitable risk.

The Solution: How Cloud Attack Emulation Addresses The Confusing Dimensions
Cloud Attack Emulation systematically addresses all three dimensions of confusion by providing a comprehensive approach that bridges the gaps in CSPM, traditional ppenetration testing, and production-ready cloud security validation.
Solving Dimension 1: Bridging CSPM and Penetration Testing
CSPM tools excel at identifying misconfigurations and compliance gaps, but they leave critical questions unanswered: Which findings are actually exploitable? Can attackers chain these issues into real attacks? Will your detective controls catch malicious activity? Cloud Attack Emulation bridges this gap by transforming CSPM's theoretical findings into empirical evidence. Specifically, it addresses the four fundamental limitations of CSPM by validating what CSPM can only theoretically identify.
Addressing Point-in-Time Limitations: While CSPM provides snapshots of your environment, Cloud Attack Emulation enables continuous validation through scheduled and on-demand testing. Mitigant CAE supports daily, weekly, or triggered attack execution to validate cloud security posture as the cloud infrastructure evolves. This continuous approach catches new vulnerabilities introduced by infrastructure-as-code deployments, auto-scaling events, or service launches that occur between CSPM scans.
Solving the Validation Gap: Cloud Attack Emulation transforms theoretical CSPM findings into empirical evidence. When CSPM identifies an S3 bucket with public access or an overly permissive IAM role, Mitigant CAE attempts exploitation in a controlled and safe manner. This proves whether the misconfiguration is genuinely exploitable or mitigated by other controls. More importantly, it tests whether attackers can chain multiple permissions together to escalate privileges, move laterally, and access critical resources; answering the questions CSPM cannot.
Validating CSPM Attack Paths: Modern CSPM tools use approaches like graph analytics to visualize theoretical attack paths and calculate blast radius. Mitigant CAE validates these paths by attempting to traverse them. When a graph shows a path from an internet-exposed Lambda function to an RDS database containing customer data, Mitigant CAE determines whether VPC policies, security groups, network ACLs etc, block that path. This eliminates false positives by distinguishing between paths that look exploitable on paper and paths that are genuinely exploitable.
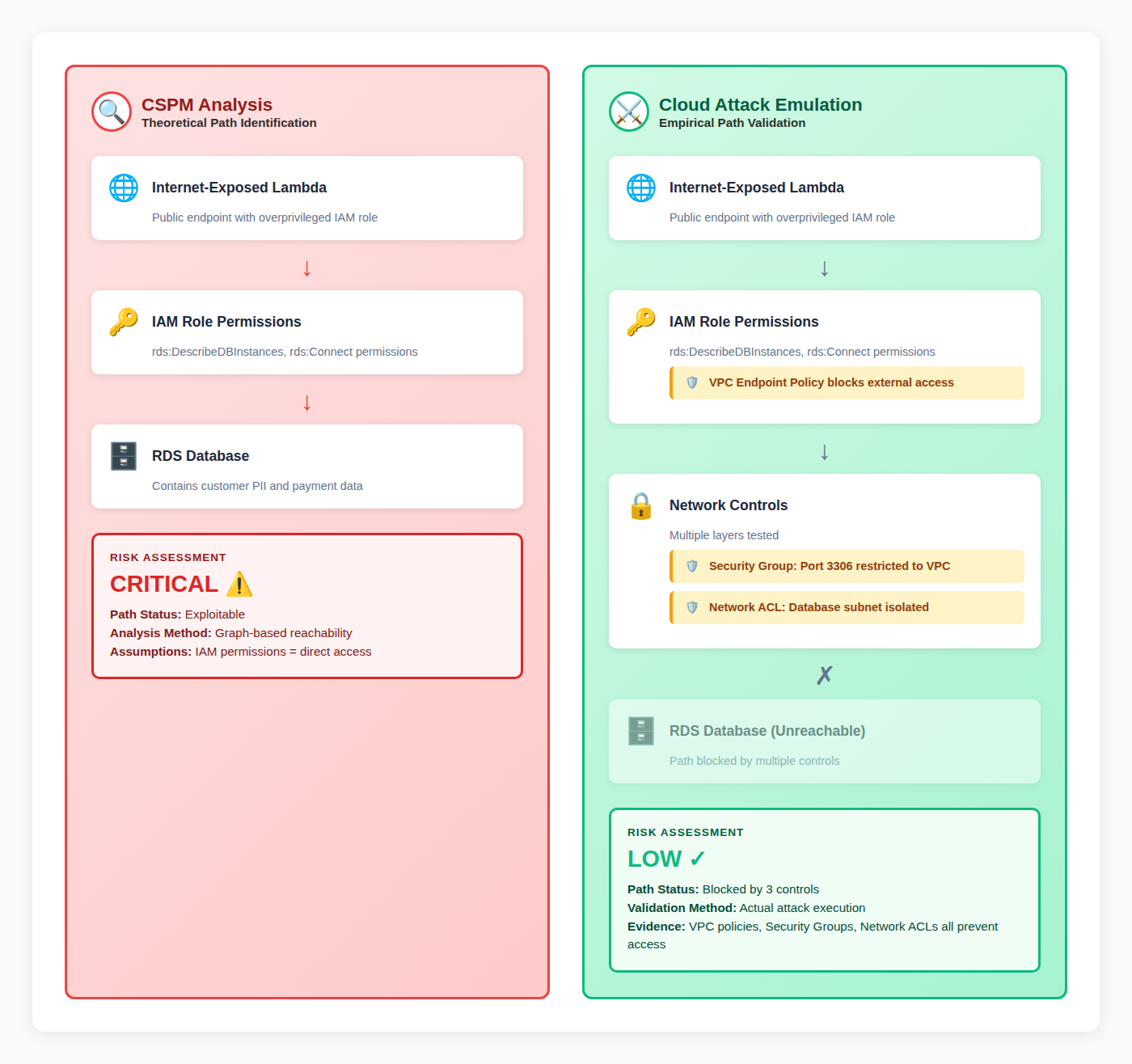
Testing Security Control Effectiveness: CSPM reports whether CloudTrail is enabled and whether SIEM rules exist, but Mitigant CAE validates whether these controls actually work. During attack execution, the Mitigant CAE monitors whether threat detection control generate alerts. For example, Mitigant CAE validates if Cloud Threat Detection services like GuardDuty and Azure Defender/Microsoft Sentinel detect emulated attacks, which helps to confirm if SOC team receive actionable notifications. Telemetry from these services are also retrieved as evidence, showing exactly what was detected and what was missed and allowing for effective tuning of detection rules.
Solving Dimension 2: Production-Ready Testing with Mitigant's Hybrid Approach
Mitigant CAE addresses the lack of automated tools for safely testing existing resources with an innovative hybrid methodology that achieves both realism and safety without compromise, ultimately solving the tool gap that has plagued cloud security testing:
Inline Attacks: These are attacks capable of targeting deployed cloud resources such as S3 buckets, EC2 instances, Lambda functions, and IAM resources.Inline attacks provide unmatched realism as it allows safe and realistic testing of the cloud security posture, not a theoretical replica. When CSPM identifies a misconfiguration, inline attack emulation determines whether the issue is exploitable or merely theoretical noise.
Provisioned Attacks: These attacks create temporary, isolated infrastructure specifically for testing techniques that could cause service disruption or data loss. Mitigant CAE automatically spins up controlled resources, executes specific attacks, collects comprehensive telemetry, and cleans up the infrastructure afterward. This attack strategy enables aggressive testing of risky attack techniques while maintaining complete safety.

This hybrid methodology represents a fundamental advancement over both traditional penetration testing (which avoids production) and breach-and-attack simulation tools (which use completely isolated environments). Security teams get the realistic validation they need without the operational risk they fear, enabling the continuous testing that modern cloud security demands. Moreover, this approach eliminates the compliance-driven checkbox mentality by providing genuine security validation that goes beyond satisfying audit requirements.
Solving Dimension 3: Cloud-Native Continuous Testing
Mitigant CAE addresses the limitations of traditional penetration testing by providing cloud-native approaches tailored to modern cloud infrastructure. It tests attack paths by chaining multiple techniques, validates both preventive and detective controls, and cover hundreds of cloud-specific attack techniques. Furthermore, Mitigant CAE aggregates evidences to provide concrete proof of exploitability and maps findings to MITRE ATT&CK techniques.
The rapid test-fix-retest cycle validates that remediations actually work and don't introduce new vulnerabilities. Unlike traditional point-in-time pentesting that requires scheduling consultants weeks in advance, cloud attack emulation operates continuously, with scheduled testing, API-driven automation for CI/CD integration, on-demand execution, and the ability to parallelize multiple attack scenarios. This transforms security validation from an annual exercise into a continuous practice that keeps pace with the dynamic nature of cloud environments, and the rapidly evolving threat landscape.
By combining CSPM's comprehensive configuration visibility with attack emulation's empirical validation, organizations achieve a complete security validation cycle: identify potential vulnerabilities through continuous monitoring, validate actual exploitability through realistic attack testing, prove detection capability through security control validation, and rapidly verify remediation effectiveness through automated retesting. This integrated approach transforms security from hope-based (hoping configurations are secure) to evidence-based (knowing which attacks succeed and which defenses work).
Why Mitigant Delivers Unique Value
Mitigant provides a single, unified platform that integrates CSPM and adversary emulation, eliminating context switching between tools and simplifying procurement with a single vendor and a single contract. The platform guarantees production safety through non-destructive attacks that validate exploitability without causing damage, with automated safeguards preventing accidental resource deletion and built-in rollback capabilities for automatic cleanup. Unlike external penetration testing that requires cloud provider approval, Mitigant operates entirely within your cloud tenant using your credentials, allowing you to test as frequently as needed without notification requirements or waiting periods.
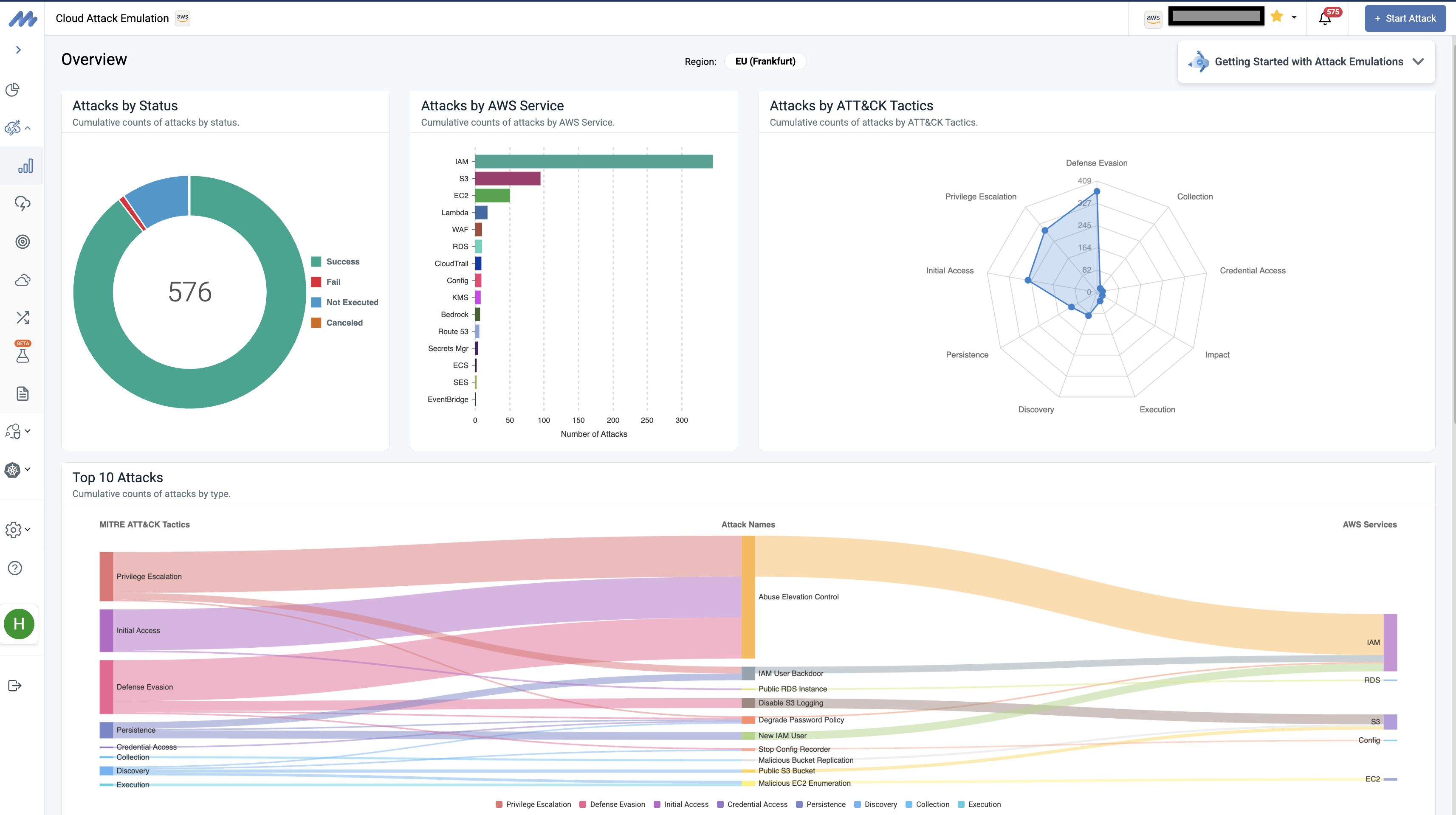
The platform offers comprehensive attack coverage with over 200 cloud-native managed attack scenarios mapped to MITRE ATT&CK and MITRE ATLAS, including multi-cloud attack chains spanning AWS, Azure, and hybrid environments. Beyond managed attacks, Mitigant's Attack Builder feature empowers security teams to write custom attacks tailored to their specific threat models, unique infrastructure configurations, or emerging threat intelligence, enabling organizations to go beyond pre-built scenarios and validate defenses against organization-specific attack patterns.
Remediation validation is effortless with a built-in rerun capability that provides one-click retesting of previously executed attacks, immediate validation of fixes, and historical comparison to track improvements over time. The platform is fully automated, with scheduled testing, API-driven CI/CD integration, on-demand execution, and parallel testing of multiple scenarios. Most importantly, Mitigant retrieves attack evidence directly from CloudTrail and Azure Activity Logs to validate attack outcomes, providing objective evidence of what worked, what failed, and what was detected.
Conclusion
CSPM scans and cloud penetration testing serve complementary but fundamentally different purposes. CSPM identifies potential vulnerabilities through configuration auditing—an essential first step. Real cloud penetration testing validates exploitability, tests defenses, and provides evidence of actual risk.
The confusion exists across three dimensions: misunderstanding what each technology does, lack of production-ready testing tools, and the poor fit of traditional pentesting for cloud. This creates a dangerous gap where organizations believe they're protected after configuration auditing alone.
Mitigant Cloud Attack Emulation systematically addresses all three dimensions through its innovative hybrid approach—bridging CSPM and pentesting, providing production-ready tooling, and enabling continuous cloud-native validation. The result: evidence-based security that proves which attacks succeed and which defenses work.
Ready to validate your cloud security in minutes, not months? Sign up for a free trial or join our public beta for early access of the Attack Builder.
👉 Start your free trial | Join the public beta






.png)
